[CD] HawkEye
Scenario
An accountant at your organization received an email regarding an invoice with a download link. Suspicious network traffic was observed shortly after opening the email. As a SOC analyst, investigate the network trace and analyze exfiltration attempts.
Questions
Q: How many packets does the capture have?
A: 4003
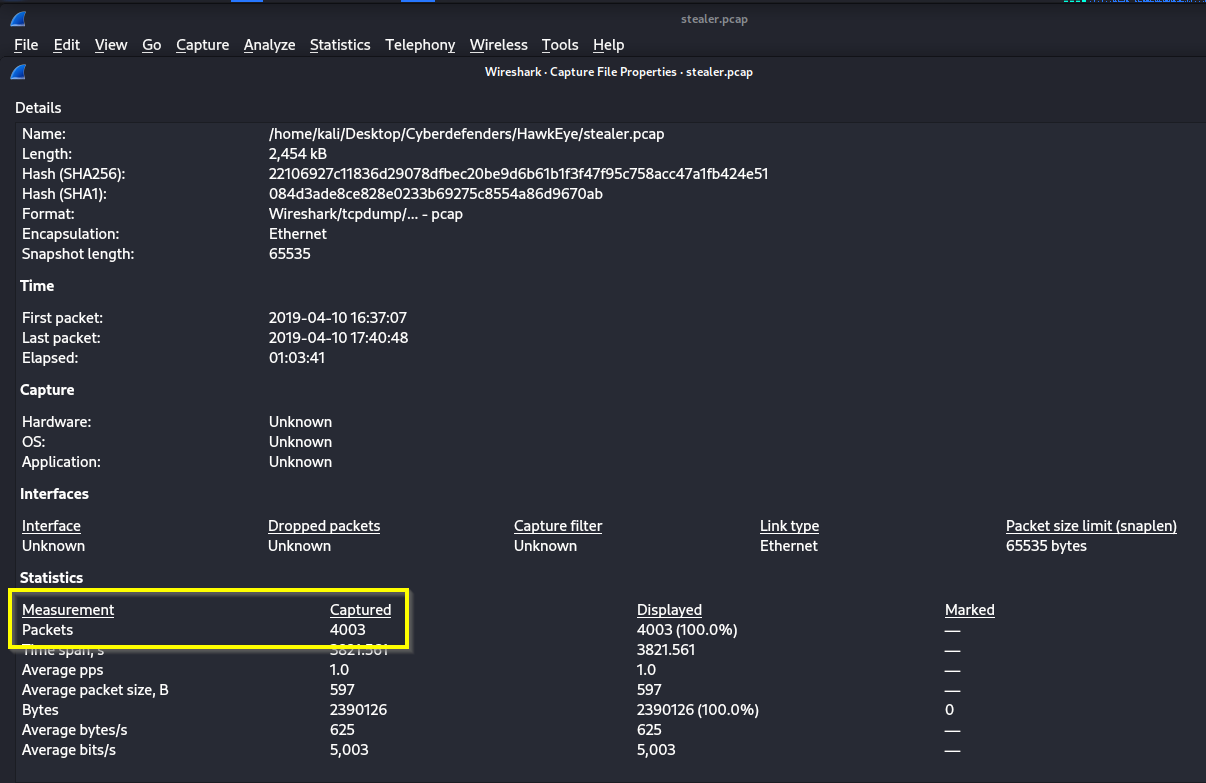
Q: At what time was the first packet captured?
A: 2019-04-10 20:37:07 UTC
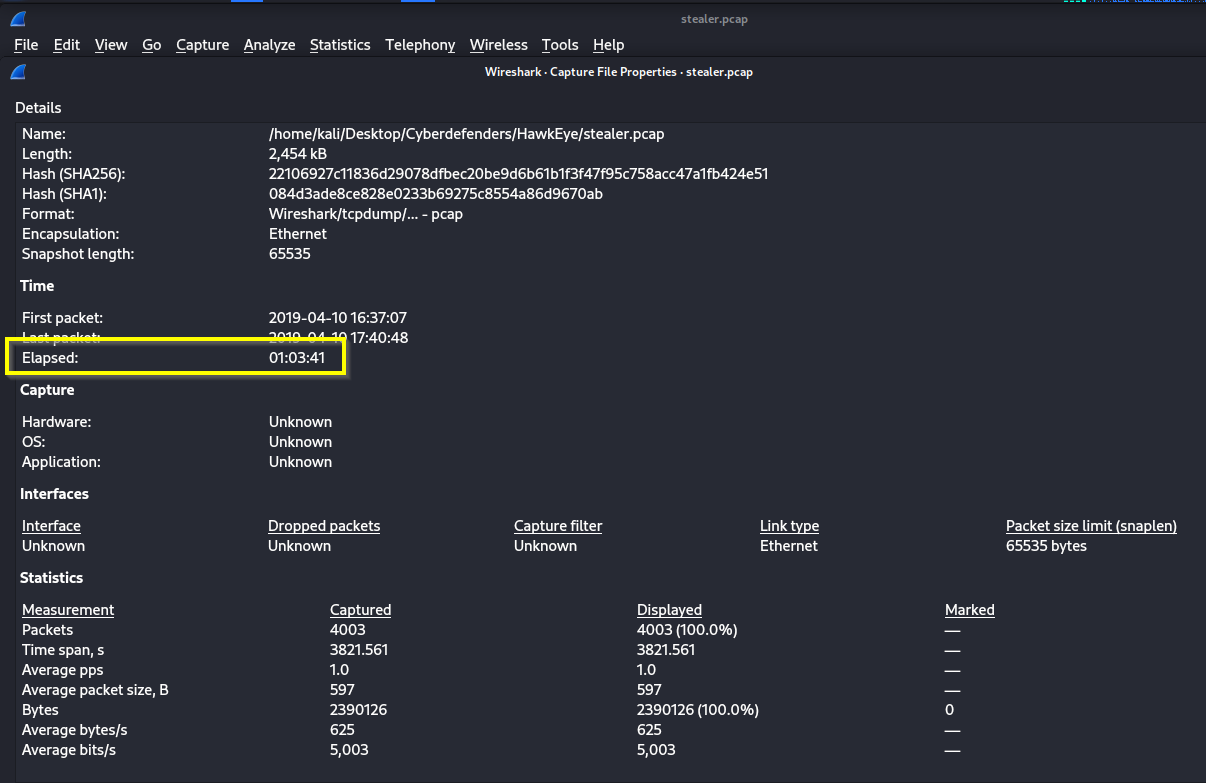
Q: What is the duration of the capture?
A: 01:03:41
Q: What is the most active computer at the link level?
A: 00:08:02:1c:47:ae
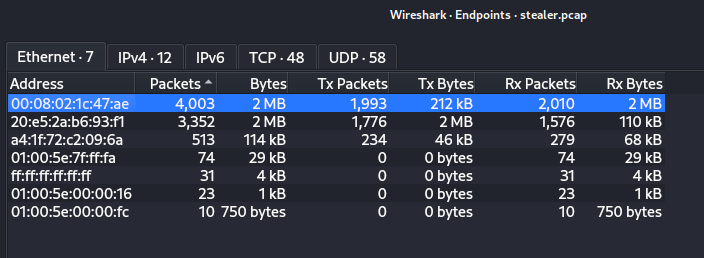
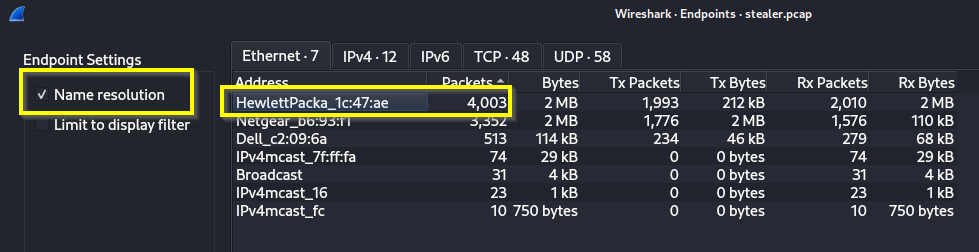
Q: Manufacturer of the NIC of the most active system at the link level?
A: Hewlett-Packard
Q: Where is the headquarter of the company that manufactured the NIC of the most active computer at the link level?
A: Palo Alto
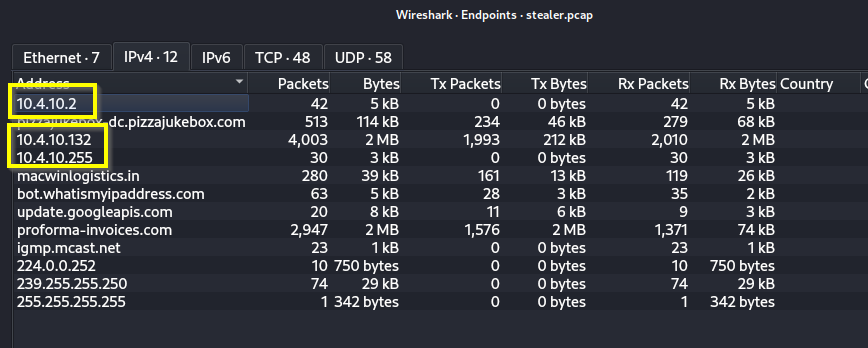
Q: The organization works with private addressing and netmask /24. How many computers in the organization are involved in the capture?
A: 3
Q: What is the name of the most active computer at the network level?
A: BEIJING-5CD1-PC
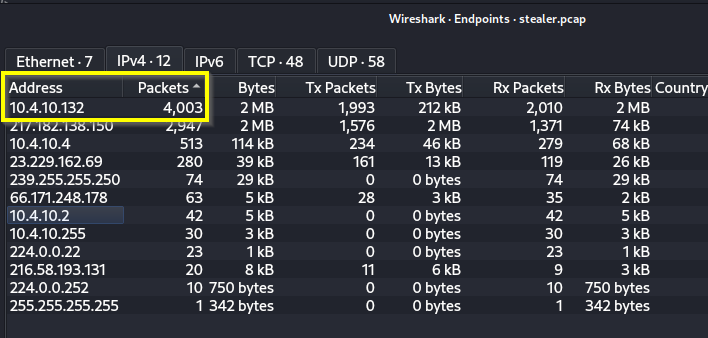
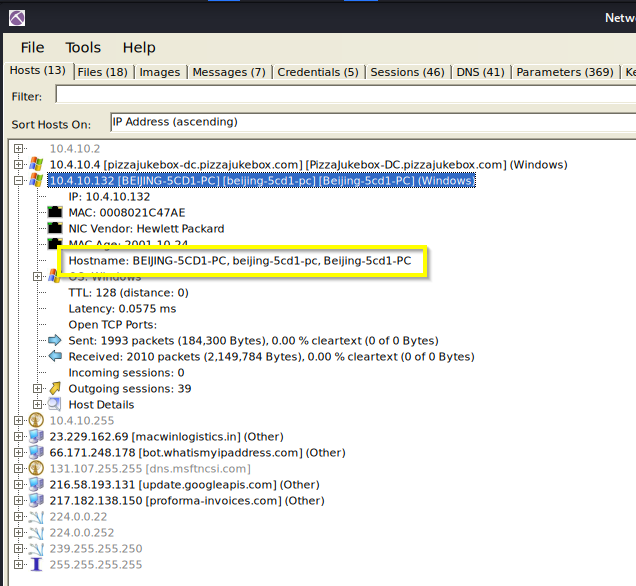
Q: What is the IP of the organization’s DNS server?
A: 10.4.10.4
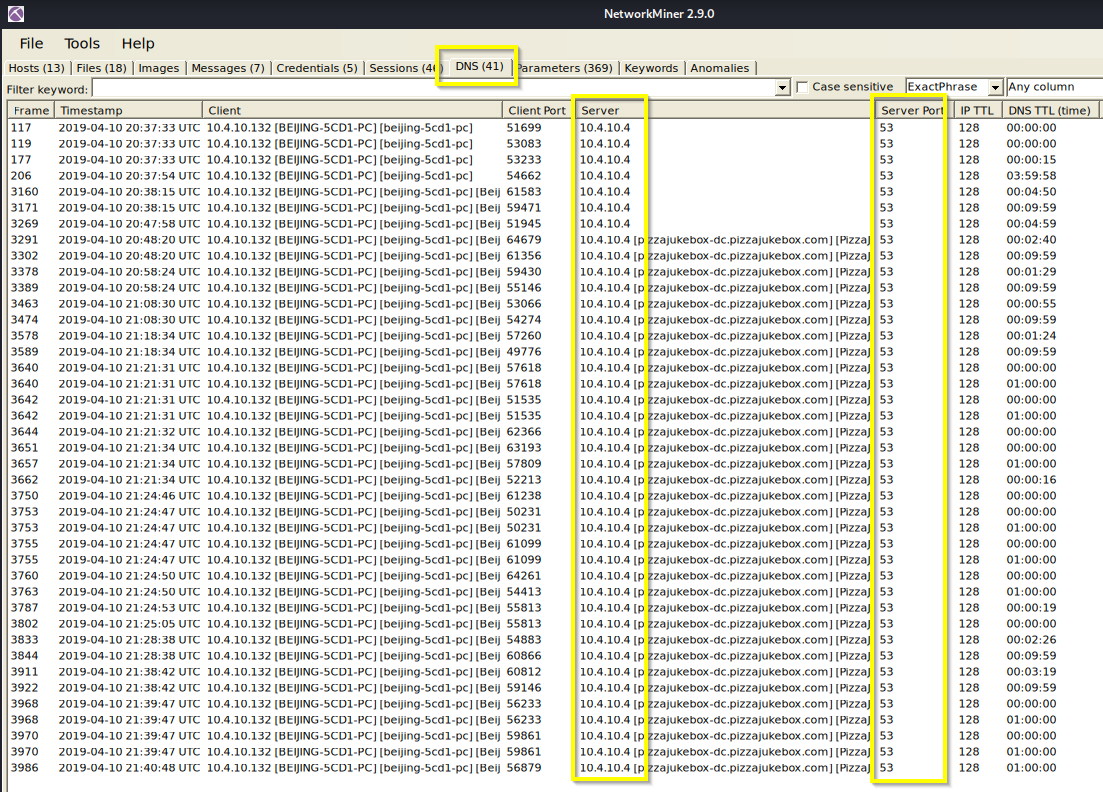
Q: What domain is the victim asking about in packet 204?
A: proforma-invoices.com
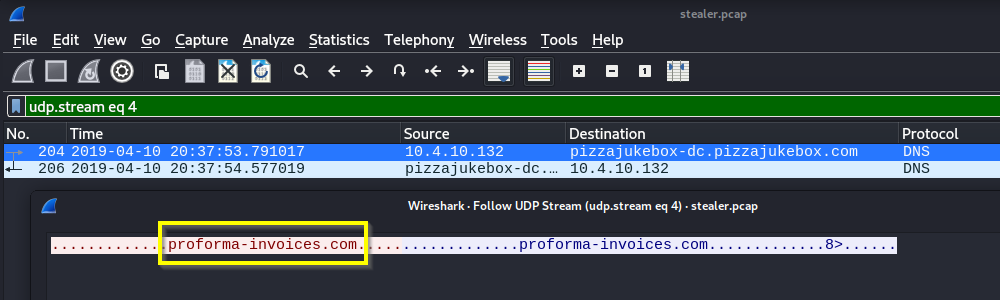
Q: What is the IP of the domain in the previous question?
A: 217.182.138.150
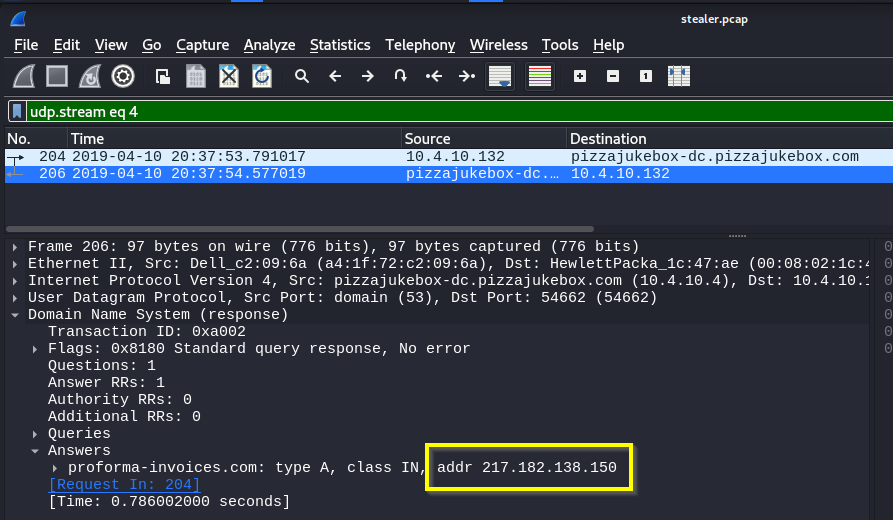
Q: Indicate the country to which the IP in the previous section belongs.
A: France
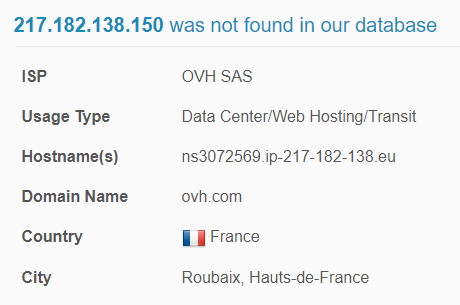
Q: What operating system does the victim’s computer run?
A: Windows NT 6.1
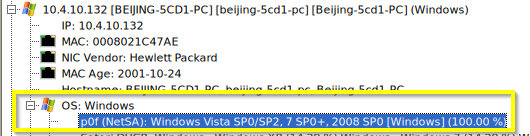
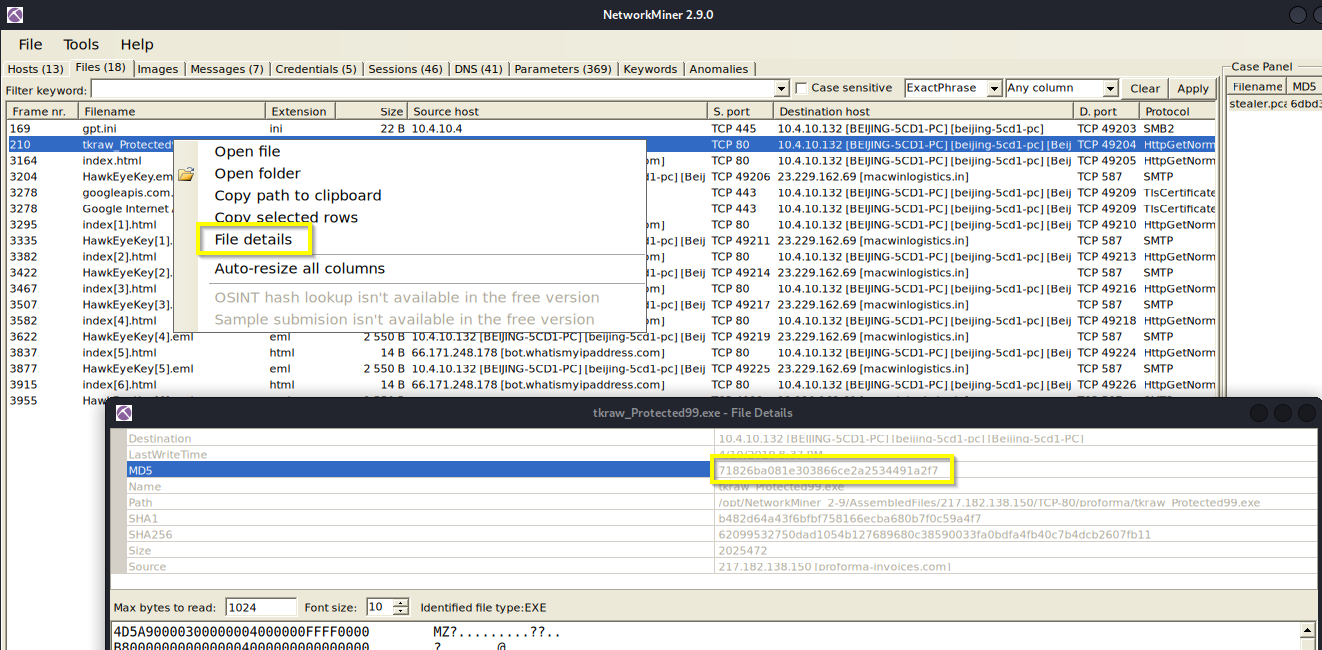
Q: What is the name of the malicious file downloaded by the accountant?
A: tkraw_Protected99.exe
Q: What is the md5 hash of the downloaded file?
A: 71826ba081e303866ce2a2534491a2f7
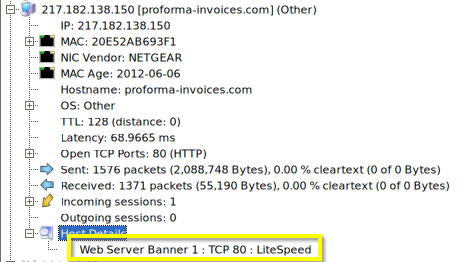
Q: What software runs the webserver that hosts the malware?
A: LiteSpeed
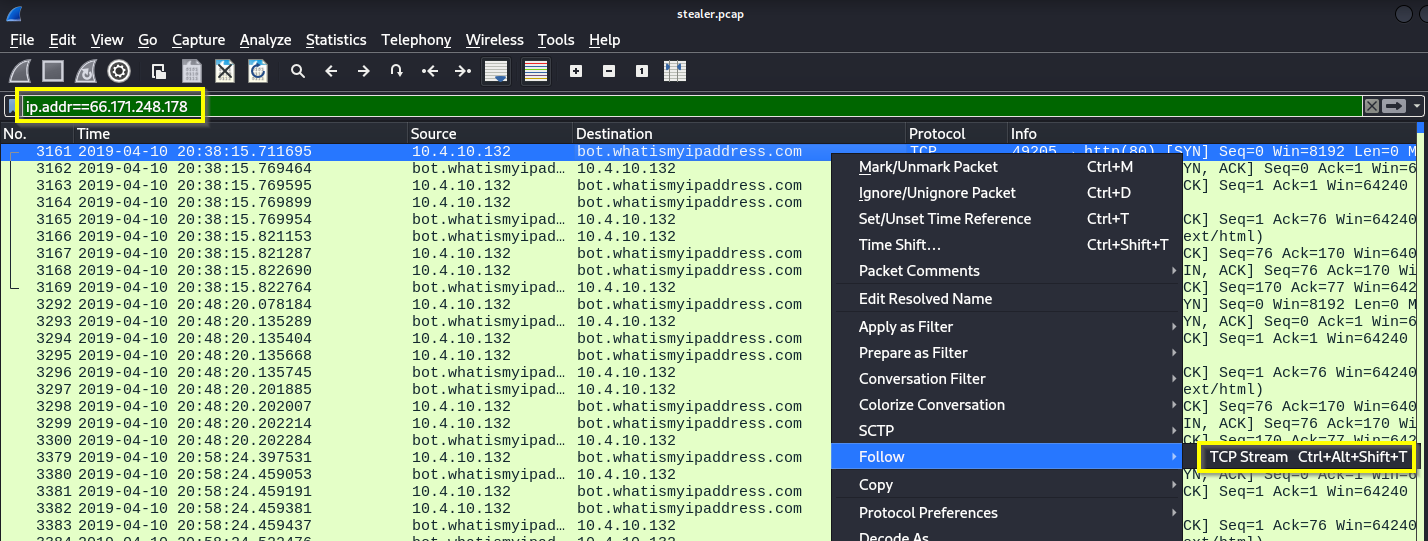
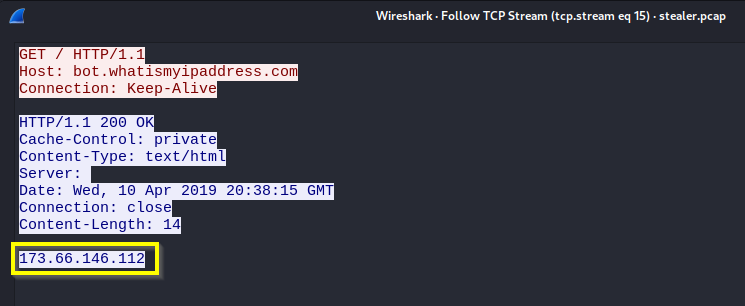
Q: What is the public IP of the victim’s computer?
A: 173.66.146.112
Q: In which country is the email server to which the stolen information is sent?
A: United States
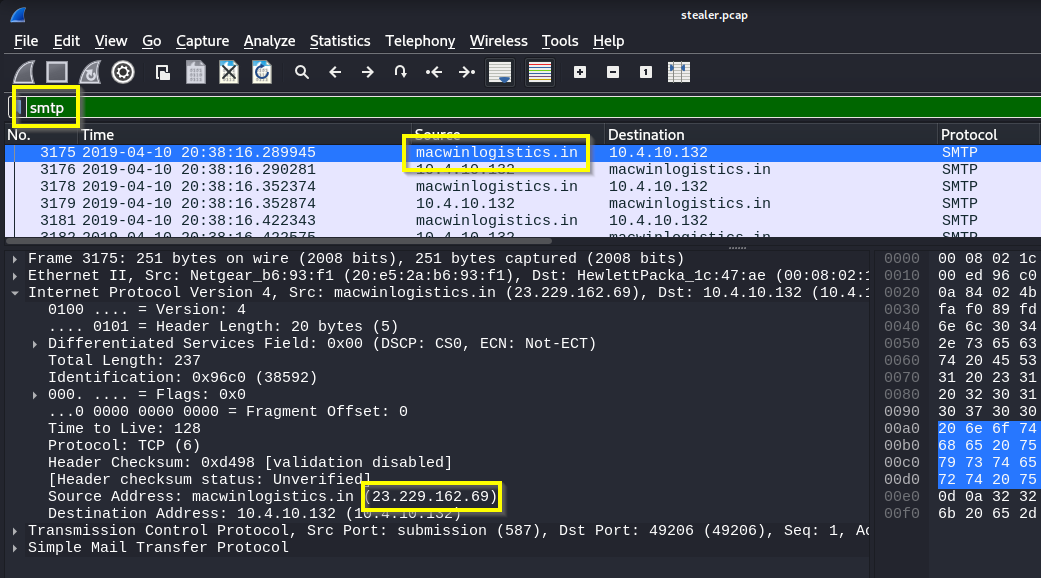
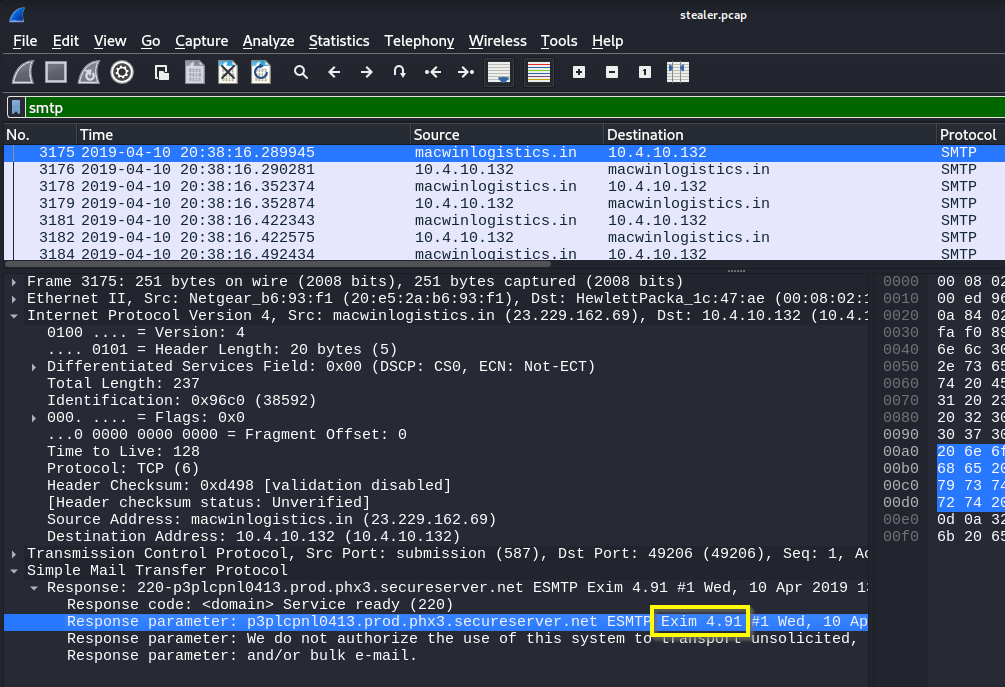
Q: Analyzing the first extraction of information. What software runs the email server to which the stolen data is sent?
A: Exim 4.91
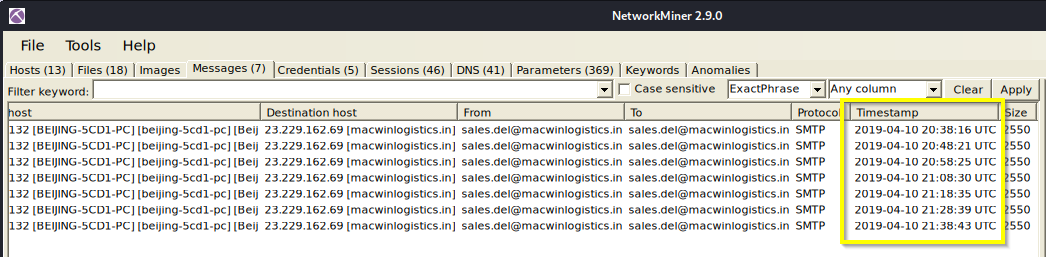
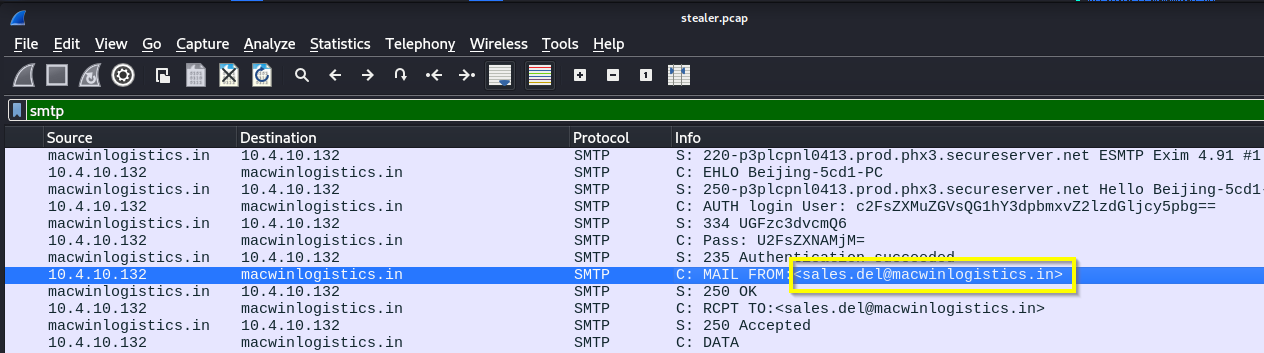
Q: To which email account is the stolen information sent?
A: sales.del@macwinlogistics.in
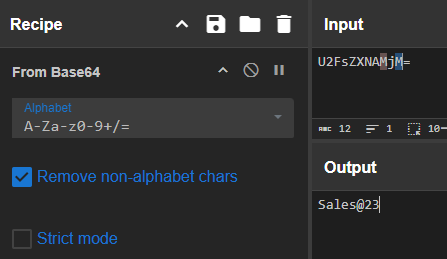
Q: What is the password used by the malware to send the email?
A: Sales@23
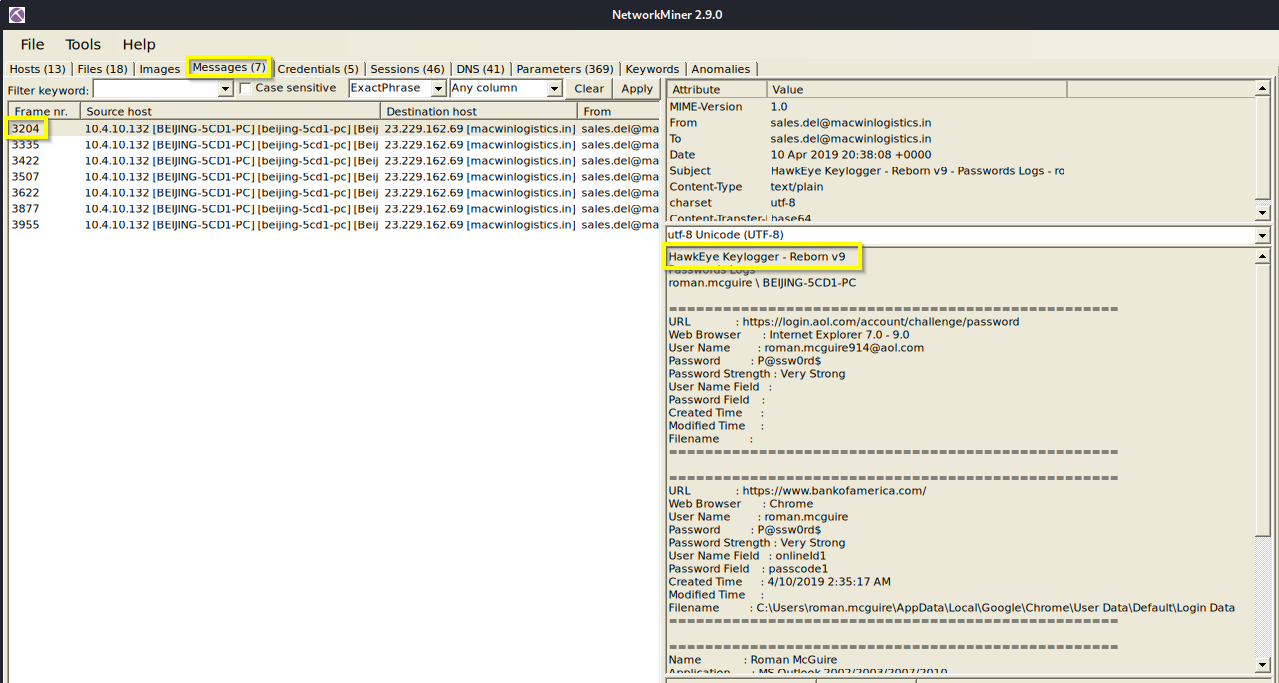
Q: Which malware variant exfiltrated the data?
A: Reborn v9
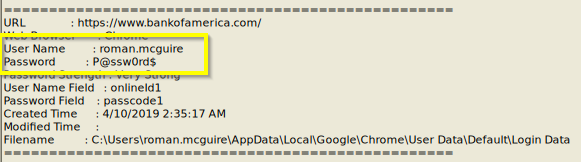
Q: What are the bankofamerica access credentials? (username:password)
A: roman.mcguire:P@ssw0rd$
Q: Every how many minutes does the collected data get exfiltrated?
A: 10